The "Meta Pixel" Vulnerability: How a Third-Party Script Led to Account Takeover

We've all been there, copying a third-party script tag, pasting it into our website's header, checking that it works, and calling it a day. Google Analytics? Check. Meta Pixel? Check. These tools are supposed to be the easy part of web development. But as security researcher Youssef Sammouda discovered in October 2024, sometimes the "trusted" scripts we rely on can become our biggest liability.
This case study walks you through a fascinating vulnerability in Meta's fbevents.js script, a flaw that allowed attackers to steal Instagram OAuth codes and take over user accounts. All it took was exploiting one poorly validated message listener.
What is the Vulnerability?
If you've ever run Facebook or Instagram ads, you know the Meta Pixel. It's that small JavaScript file (fbevents.js) installed on millions of websites worldwide to track conversions, measure campaigns, and understand user behavior.
To do its job effectively, the Meta Pixel needs to communicate across different windows and domains. That means it listens for messages from popups, iframes, and other browser contexts using the postMessage API. This is standard practice for modern web analytics.
But here's where things went wrong: The script accepted messages a bit too trustingly. It didn't properly verify who was sending these messages. The assumption seemed to be: "If we're running on a Facebook domain, we're probably safe." That assumption turned out to be dangerously wrong.
How the Attack Works
What makes this vulnerability particularly interesting is how the attacker chained together several seemingly harmless behaviors to achieve something critical: complete account takeover. Let's walk through each step.
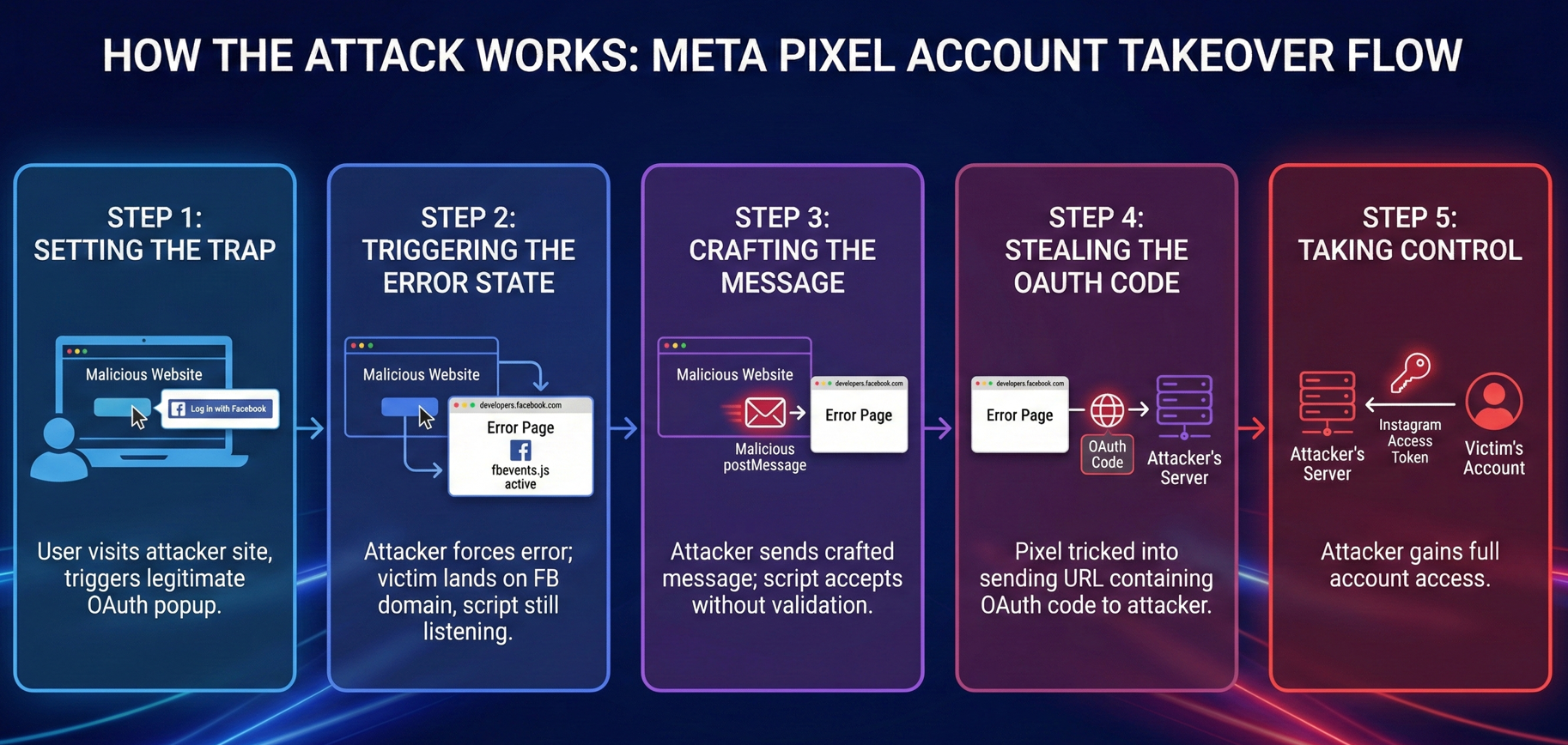
Step 1: Setting the Trap
The attacker starts by creating a malicious website. Nothing fancy, just a page that can open popups and send messages. When an unsuspecting user visits this site, it triggers a legitimate Meta OAuth popup window. You know, the "Log in with Facebook" or "Log in with Instagram" flow that we see everywhere.
At this point, everything looks normal. The victim sees a real Facebook login window, and nothing seems suspicious.
Step 2: Triggering the Error State
Here's where the cleverness begins. Instead of letting the OAuth flow complete naturally, the attacker deliberately sends an invalid nonce parameter. This causes the authentication to fail, landing the victim on an error page hosted at developers.facebook.com.
Now you might think, "So what? It's just an error page." But here's the critical detail: even though it's an error page, the fbevents.js script is still loaded and actively listening for messages. The victim is now on a trusted Facebook domain, and the attacker's original page still has a reference to this window through window.opener.
Step 3: Crafting the Malicious Message
This is the heart of the exploit. The attacker's malicious website sends a carefully crafted postMessage to the error page window. Because fbevents.js didn't properly validate the message's origin, it accepted this external message as legitimate.
The script was essentially tricked into thinking: "This must be a valid tracking event from our own system."
Step 4: Stealing the OAuth Code
Once the malicious message was accepted, the attacker could manipulate the Meta Pixel into making a network request to graph.facebook.com. The crucial part? This request automatically included the current page's URL and referrer information.
Remember, the victim was still in an OAuth flow (even though it had errored out). That means the URL contained sensitive query parameters, specifically, the OAuth authorization code. By manipulating the pixel to send this "event" to an attacker-controlled Pixel ID, the script effectively handed over the victim's authentication credentials.
Step 5: Taking Control
With the OAuth code in hand, the attacker could exchange it for a valid Instagram access token. Game over. Full account access achieved.
Meta's Response: The vulnerability was responsibly disclosed and patched. Youssef Sammouda received a bounty of $32,500 for this finding.
Developer Best Practices
If there's one pattern you should watch for in your own code (or in third-party scripts you use), it's this: insecure postMessage listeners.
When reviewing JavaScript files, whether manually or using automated tools like Jsmon, be alert for code that looks like this:
window.addEventListener('message', function(event) {
// DANGER: No origin check
// DANGER: Blindly trusting the data
processMessage(event.data);
});This is a recipe for disaster. Any website can send messages to any other website. Without proper validation, you're essentially leaving your front door unlocked.
Here's what secure message handling looks like:
window.addEventListener('message', function(event) {
// ALWAYS validate the sender's origin
if (event.origin !== "<https://trusted-site.com>") {
return; // Reject the message
}
// Now it's safe to process the data
processMessage(event.data);
});The fix is simple, but it's often overlooked, especially in complex third-party libraries that need to handle messages from multiple sources.
Why Third-Party Scripts Matter
This case study highlights something that doesn't get enough attention: third-party scripts inherit your application's security context.
You might spend months hardening your own codebase, implementing CSP headers, sanitizing inputs, following OWASP guidelines. But if you load a vulnerable third-party library, all that work can be undermined. The Meta Pixel runs with the same privileges as your own JavaScript. Its vulnerabilities become your vulnerabilities.
For security researchers and bug bounty hunters, this case is also instructive. Sometimes the most lucrative vulnerabilities aren't in the "sexy" parts of an application. They're in the boring tracking scripts and analytics tools that everyone assumes are bulletproof.
How We Can Help
Finding vulnerabilities like this requires visibility into what's actually running on your web properties. You need to know:
- What third-party scripts are loaded on your pages
- When those scripts change or update
- What risky patterns exist in your JavaScript codebase
- Whether sensitive data is being exposed through client-side code
That's exactly what Jsmon.sh was built for. It helps you analyze and monitor JavaScript files at scale, giving you the ability to detect dangerous patterns, track third-party script changes, and catch potential vulnerabilities before they're exploited in the wild.
Whether you're a security researcher hunting for bugs or a development team trying to secure your business, having real-time visibility into your JavaScript attack surface isn't optional anymore, it's essential.
Secure your business, in real-time.