S3 Bucket Takeover in H1702 LHE Worth $3000 Via Jsmon.sh

I was sitting on the last day of the H1702 Epic Games event. I've submitted a few bugs to Epic Games and it was the last day, I was not getting any idea on what else to submit. I decided to use my own product jsmon.sh.
Collecting JS Files
This is how I collected the JS files for Epic Games.
- Opened the burpsuite project, click on HTTP history, click on Filter Settings. In Filter by file extension: tick on Show only and type in
js. Enable Show only in-scope items if you've scope set as well. Apply it. Now you'll only see the JS files, select all byCtrl+Aand copy the selected URLs. Save them in a notepad asjsurls.txt. - Use gau with all the providers to collect the JS files and extra grep filter for JS files.
cat domains.txt | gau --providers wayback,commoncrawl,otx,urlscan --mt
'text/javascript' --o gau.txt; cat gau.txt | grep -E '\.js' |
anew jsurls.txt- In the above command, domains.txt is the file containing all the in-scope domains for Epic Games. I am using gau to extract archived URLs from 4 providers here and using
--mtflag to match by the MIME typetext/javascriptand saving the file asgau.txt. Then, using grep filter.jsand appending the JS URLs in the same filejsurls.txt.
JS URLs into jsmon.sh
I had around 1831 JS files at this point and now it's time to pipe them into jsmon.sh. There are two ways I can do this today.
- Using jsmon-cli:
cat jsurls.txt | parallel -j 5 ./jsmon -uploadUrl {} - By directly uploading the file on jsmon.sh: Split the file into two parts 1000 and 831. The maximum limit currently set on jsmon.sh is 1000 JS urls. Upload both files.
Jsmon-CLI is a Golang client created by our team to interact with the API on CLI. Here's the link to install the CLI: https://github.com/rashahacks/jsmon-cli.
I did it the first way during LHE because our file service has some maintenance fixes remaining.
JS Intelligence Results
It was time to finally fetch results from JS Intelligence. There are various attributes which jsmon extracts like domains, emails, IP addresses, URLs, API paths, etc. It also extracts the S3 buckets and S3 bucket takeovers automatically.
I went to the JS Intelligence section and I was able to see a +1 entry in my S3 bucket takeovers tab. I was like huhhh?? Opened it, and found that yesss, there's a JS URL from one of the Epic Games acquisitions which contains an available S3 bucket.
Taken over the bucket and shown the impact on how the attacker can point it to the media asset where the JS file is referencing it.
Conclusion
Collected JS files from as many sources as possible for the target. Uploaded all of them into jsmon.sh for data extraction. Used the JS Intelligence data and found a S3 bucket takeover.
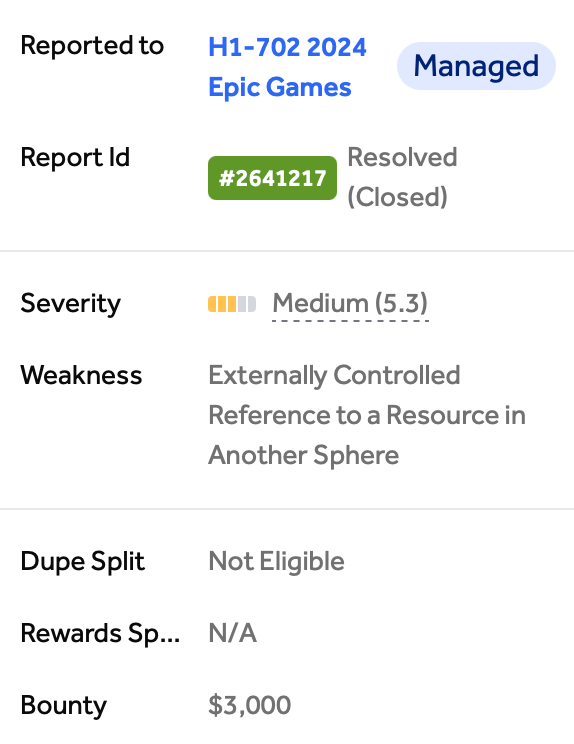
Reporting
- Reported on 5th August 2024
- Triaged on 8th August 2024
- Paid 3000$ on 18th Sept 2024
Thanks,
Inderjeet Singh, Founder@jsmon.sh