What is PII Data? Types of PII, Examples & Risks
What is PII Data? PII (Personally Identifiable Information) includes data that can identify a person—names, emails, phone numbers, Aadhaar, SSN, IPs, and more. Learn PII types, examples, and risks.
Most security teams are laser-focused on hunting for API keys, tokens, and credentials. And for good reason, leaked secrets can grant instant access to critical systems. But here's the uncomfortable truth: while everyone's busy scanning for AKIA... patterns, there's a different kind of threat slipping through the cracks. One that doesn't expire, can't be rotated, and carries consequences that last a lifetime.
We're talking about Personally Identifiable Information (PII).
It's Not Just About API Keys
Think about it this way: when an AWS access key leaks, you rotate it. Crisis averted in minutes. But what happens when a Social Security Number leaks? Or medical records? Or a database dump containing thousands of customer email addresses paired with their purchase histories?
You can't rotate a person's identity.
PII leaks are what I call "silent killers." They don't trigger your monitoring alerts. They won't crash your servers or spike your error rates. But they can trigger regulatory nightmares, massive fines, and the kind of reputation damage that takes years to recover from, if you ever do.
The reality is that most bug bounty hunters and security teams are trained to flag exposed API keys, but they often scroll right past data dumps containing names, addresses, phone numbers, or medical information. It's a blind spot we can't afford to have anymore.
What Is PII Data?
Let's start with the basics. PII stands for Personally Identifiable Information, and the definition is simpler than most compliance documents make it sound:
PII is any information that can be used to distinguish or trace an individual's identity, either on its own or when combined with other data.
Here's where it gets interesting: context matters. A lot.
The name "John Smith" by itself? Pretty harmless. There are thousands of John Smiths out there. But "John Smith" + "Lives in ZIP code 90210" + "Date of Birth: March 15, 1985"? Now you've got something that can uniquely identify someone. And if you add "Diagnosis: Stage 2 Diabetes" to that mix? You've just leaked highly sensitive medical information that could impact someone's insurance, employment, and personal life.
This is why understanding PII isn't just about memorizing a list of "bad" data types. It's about understanding how seemingly innocent pieces of information can combine to create a complete picture of someone's identity.
Types of PII Data
Not all PII works the same way. Security professionals generally break it down into two categories:
Direct Identifiers (Linked PII)
These are data points that immediately identify a specific person without needing any additional context. If you see one of these leaked in the wild, alarm bells should be ringing:
- Social Security Numbers (SSN) – The holy grail of identity theft
- Passport Numbers – Unique to each individual globally
- Driver's License Numbers – Government-issued identification
- Full Face Photographs – Biometric identification
- Fingerprints – Unchangeable biometric data
When these leak, there's no ambiguity. Someone's identity is compromised, period.
Indirect Identifiers (Linkable PII)
These are trickier. On their own, they might seem innocuous. But combine two or three of them, and suddenly you can pinpoint exactly who someone is:
- Date of Birth – Narrows down possibilities significantly
- ZIP Code – Geographic identification
- Race or Ethnicity – Demographic data
- IP Address – Can reveal location and identity
- Device ID or IMEI – Unique hardware identifiers
Here's a real-world example: researchers once demonstrated that just three data points, ZIP code, birth date, and gender, were enough to uniquely identify 87% of the U.S. population. That's the power (and danger) of linkable PII.
PII Compliance and Regulations
This is where things get really important for organizations. Different types of PII trigger different regulatory frameworks, and the penalties for non-compliance can be catastrophic. Let's break down the major compliance requirements:
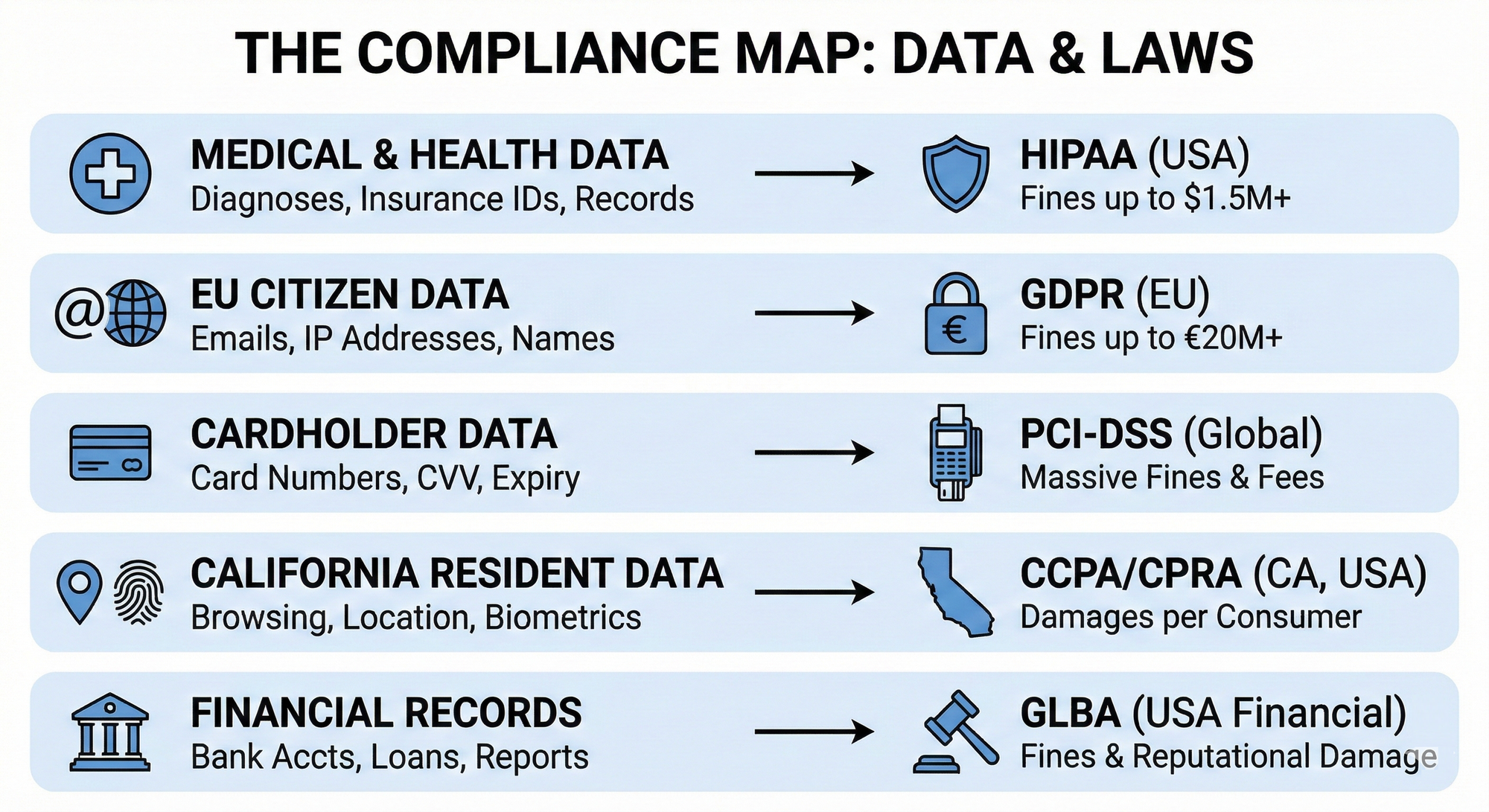
Medical & Health Data
Data types: Diagnoses, prescription information, insurance IDs, treatment records, mental health information
Regulatory framework: HIPAA (Health Insurance Portability and Accountability Act) in the United States
If you're handling anything related to someone's health, HIPAA isn't optional. Violations can result in fines up to $1.5 million per violation category per year, and in severe cases, criminal charges.
EU Citizen Data
Data types: Email addresses, IP addresses, cookie identifiers, names, location data, online identifiers
Regulatory framework: GDPR (General Data Protection Regulation) in the European Union
GDPR casts a wide net, even an email address by itself is considered personal data. The regulation applies to any organization processing data of EU residents, regardless of where your company is based. Maximum fines? Up to €20 million or 4% of global annual revenue, whichever is higher.
Cardholder Data
Data types: Credit card numbers, CVV codes, expiration dates, cardholder names
Regulatory framework: PCI-DSS (Payment Card Industry Data Security Standard)
This is a global standard enforced by the major card brands. While it's technically not a law, non-compliance can result in massive fines, increased transaction fees, and even the loss of ability to process card payments.
California Resident Data
Data types: Browsing history, geolocation data, biometric information, inferences about preferences or behavior
Regulatory framework: CCPA/CPRA (California Consumer Privacy Act and California Privacy Rights Act)
California's privacy laws are among the strictest in the U.S., and they're setting the template for other states. Violations can result in statutory damages of $100 to $750 per consumer per incident, or actual damages, whichever is greater.
Financial Records
Data types: Bank account numbers, credit reports, loan information, investment records
Regulatory framework: GLBA (Gramm-Leach-Bliley Act) in the United States
Financial institutions must protect customer data and provide clear privacy notices. While GLBA fines vary, the reputational damage from leaking financial records can be even more costly than regulatory penalties.
Severity Levels of PII Data Leaks
Not all PII leaks are created equal. When you're triaging security findings, you need to understand the real-world impact. Here's how to think about severity:
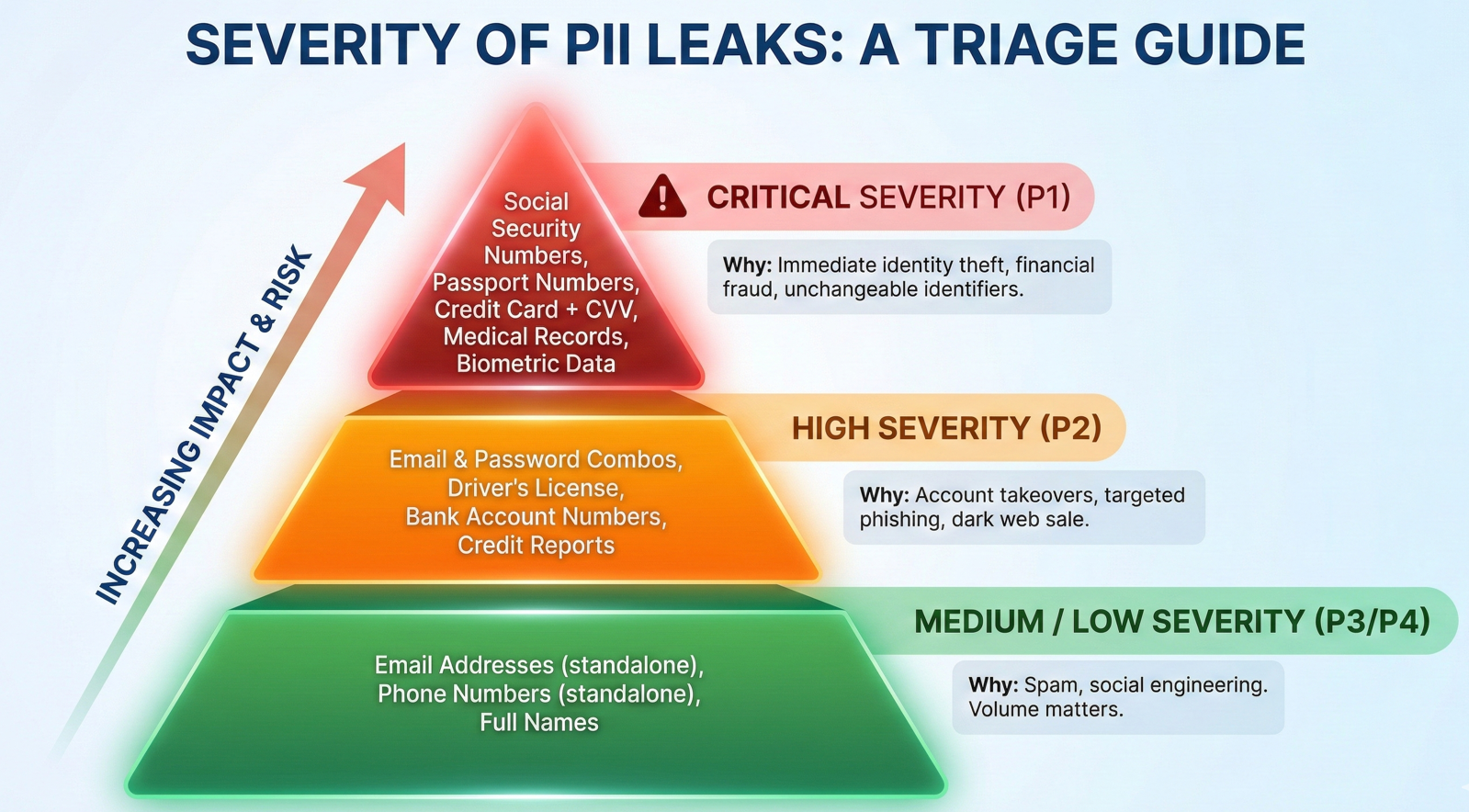
Critical Severity (P1) - Drop Everything and Fix This
Data types:
- Social Security Numbers
- Passport numbers
- Credit card numbers with CVV
- Medical records and health information
- Biometric data (fingerprints, facial recognition data, DNA information)
Why it's critical: This data enables immediate identity theft, financial fraud, and the compromise of unchangeable personal identifiers. Someone can open credit accounts, file fraudulent tax returns, or access medical services using this information. And unlike a password, victims can't just reset these identifiers.
High Severity (P2) - Fix Within Days
Data types:
- Email and password combinations
- Driver's license numbers
- Bank account numbers (without additional authentication)
- Full credit reports
Why it's high: This information enables account takeovers, targeted phishing campaigns, and can be sold on dark web markets. While the immediate risk might be lower than P1 items, the attack surface is significant.
Medium/Low Severity (P3/P4) - Fix in Regular Sprint Cycle
Data types:
- Email addresses (standalone)
- Phone numbers (standalone)
- Full names without additional context
Why it's lower: While this data can enable spam, harassment, and social engineering attempts, it doesn't directly enable identity theft or financial fraud. That said, don't ignore it entirely, especially if it's a large-scale leak. Volume matters.
Detecting PII with Jsmon
Here's where things get technically interesting. Finding leaked secrets is relatively straightforward, they follow predictable patterns. An AWS key always starts with AKIA, a Stripe key starts with sk_live_, and so on.
PII is messier.
How do you programmatically detect whether a phone number in a JavaScript file is sensitive customer data versus a hardcoded support hotline? How do you differentiate between a developer's personal email used for testing versus a leaked customer database?
This is where Jsmon comes in. Unlike simple regex scanners, Jsmon uses intelligent pattern matching combined with contextual analysis to identify potential PII leaks in JavaScript files, API responses, and configuration files. It can spot:
- Email patterns that suggest customer data dumps
- Phone number formats that match sensitive records
- Passport and ID number patterns from various countries
- Combinations of data that create indirect identifiers
The tool doesn't just flag everything and leave you drowning in false positives. It understands context and helps you prioritize what actually matters.
The Bottom Line
Here's what every security professional, developer, and bug bounty hunter needs to understand: You can't protect what you can't see.
API keys get all the attention because they're easy to find and easy to understand. But PII leaks are happening constantly, silently, and with potentially devastating consequences. A leaked API key is a fixable mistake. A leaked medical record is a permanent breach of trust.
In 2026, data privacy isn't a nice-to-have, it's a regulatory requirement, a competitive advantage, and increasingly, a matter of organizational survival.
How We Can Help
In 2026, data privacy is not optional. Jsmon.sh helps you identify and categorize sensitive PII leaks across your application before they become compliance nightmares. From hardcoded emails to exposed customer records, see what attackers see, in real-time.
Secure your business, in real-time!