OpenClaw: Security Analysis of a High-Privilege AI Agent
OpenClaw is a self-hosted, open-source autonomous AI agent designed to execute actions across local systems and external services on behalf of a user. OpenClaw introduces a high-risk control plane when operated without strict isolation and security controls.
OpenClaw is a self-hosted, open-source autonomous AI agent designed to execute actions across local systems and external services on behalf of a user. While its functionality is positioned around productivity and automation, analysis of public disclosures, third-party research, and observed deployment patterns indicates that OpenClaw introduces a high-risk control plane when operated without strict isolation and security controls.
The security concerns outlined in this analysis do not primarily arise from novel software vulnerabilities. Instead, they are consistent with architectural trust assumptions, insecure deployment patterns, and the aggregation of high-privilege capabilities into a single, long-lived agent process.
OpenClaw Overview and Operational Model
OpenClaw runs locally on a host system and is designed to interface with operating system resources, SaaS platforms, and developer tooling. Typical deployments grant the agent access to local filesystems, shell execution, browser automation, and API-driven integrations with email, chat platforms, and cloud services.
The agent maintains persistent state across sessions, including configuration data, conversation history, and operational memory stored on disk. This persistence allows OpenClaw to operate continuously and autonomously, but it also increases the impact of compromise by enabling long-term access without repeated attacker interaction.
Privilege Aggregation and Trust Boundary Collapse
OpenClaw consolidates access to multiple trust domains that are traditionally separated. Local operating system access, cloud APIs, SaaS platforms, and messaging services are mediated through a single agent process that is explicitly designed to act without continuous user confirmation.
From a security perspective, this creates a high-privilege execution environment that centralizes credentials, execution rights, and communication channels. Once control of the agent is obtained, either through direct access or indirect manipulation, the attacker inherits the full scope of permissions granted to OpenClaw.
This behavior is consistent with patterns observed in prior automation and orchestration tools where privilege aggregation, rather than software flaws, becomes the primary risk factor.
Control Plane Architecture and Exposure Risks
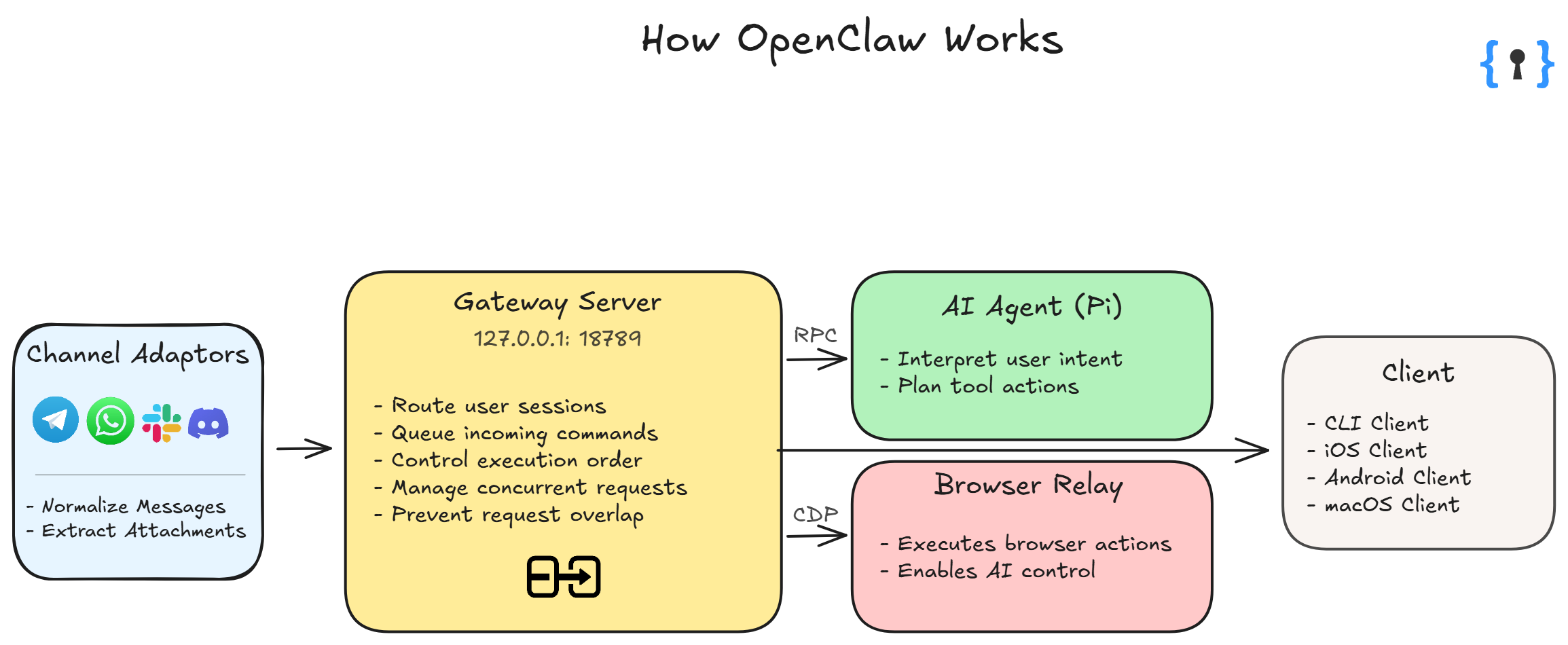
OpenClaw relies on two primary components: a web-based Control UI used for configuration and monitoring, and a Gateway service responsible for task execution, message routing, and credential handling.
The Gateway listens on a local network port and exposes both HTTP and WebSocket interfaces. By design, connections originating from localhost are treated as trusted. In practice, this assumption does not always hold in real-world deployments.
Public analysis by Jamieson O’Reilly highlights that when OpenClaw is deployed behind reverse proxies or tunnels, remote traffic may be treated as localhost. Under these conditions, authentication boundaries can collapse, potentially exposing administrative functionality.
Under such configurations, access to configuration data, stored credentials, and execution capabilities would be possible. These conditions do not stem from memory corruption or logic flaws, but from deployment configurations that collapse the distinction between trusted and untrusted access.
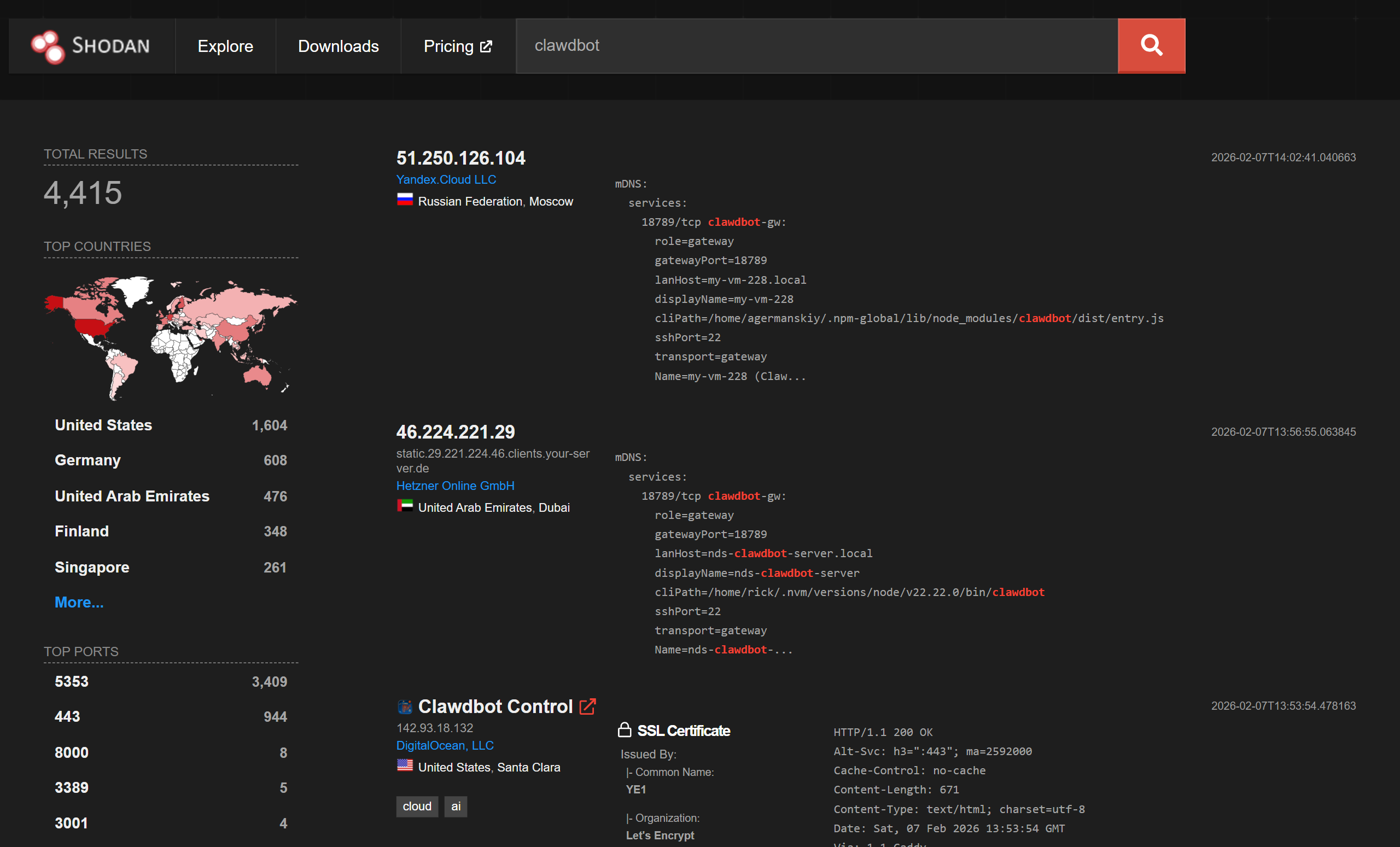
Internet Exposure and Instance Enumeration
OpenClaw services expose identifiable HTTP characteristics, including static titles and response patterns. These characteristics were sufficient for internet-wide scanning services to index OpenClaw instances shortly after deployment.
Observed indexed results included a range of configurations, from properly authenticated services to instances where authentication was missing or ineffective. While not all exposed instances were exploitable, a subset allowed unauthenticated or weakly authenticated access to administrative interfaces.
In those cases, compromise required no exploit development and could be achieved using standard HTTP or WebSocket clients.
Credential Storage and Post-Compromise Impact
OpenClaw stores sensitive material locally, including API keys, OAuth tokens, integration secrets, configuration files, and conversation history. Third-party analyses indicate that in at least some configurations, this data is stored in plaintext or recoverable formats.
Credential removal through the Control UI did not consistently eliminate all copies from disk, as backup files and historical artifacts persisted. As a result, credentials could remain accessible even after users believed they had been revoked.
From an attacker perspective, this design significantly increases post-compromise impact. Commodity infostealers targeting developer systems do not require OpenClaw-specific logic to extract these artifacts. Once harvested, credentials enabled access to email accounts, messaging platforms, source code repositories, and cloud environments.
In these scenarios, OpenClaw functioned as a credential concentration point that amplified the impact of an otherwise routine endpoint compromise.
Abuse of Untrusted Input Channels
OpenClaw processes untrusted input from email, chat platforms, documents, and web content as part of its normal operation. Analysis of agent behavior indicates that embedded instructions within such content can influence execution flow under certain conditions.
Prompt injection refers to the use of embedded instructions in otherwise legitimate content to influence an agent’s actions. This behavior does not result from a traditional software vulnerability, but from the agent’s design, where natural language input directly drives decision-making and tool invocation.
A practical example of this behavior has been documented by an independent researcher. In that case, a crafted email was delivered to a mailbox monitored by an OpenClaw instance with email integration enabled. The message embedded instructions designed to blur the boundary between user content and system guidance.
Subsequent analysis indicates that after the agent was prompted to read the latest email, it treated the embedded instructions as legitimate input. The agent then accessed multiple recent emails, summarized their contents, and transmitted that summary to an external address specified in the original message. This activity appears consistent with prompt injection behavior and did not rely on exploitation of a software vulnerability.
The underlying language model also influences exposure to prompt injection. Documentation published in the official OpenClaw GitHub repository states that while multiple models are supported, Anthropic Pro or Max tiers paired with the Opus 4.6 model are recommended due to stronger and improved resistance to prompt injection attempts.
Supply Chain Risk Through Skills and Extensions
OpenClaw supports extensibility through skills, which are commonly distributed as markdown-based instruction sets and optional scripts. Analysis of reported incidents indicates that malicious skills were used to deliver malware through social engineering rather than code exploitation.
Observed techniques included directing users to download password-protected archives, execute obfuscated shell commands, or install external dependencies hosted on attacker-controlled infrastructure. Once executed, these components ran with the same privileges as the OpenClaw agent.
Additionally, periods of project rebranding were followed by impersonation activity, including lookalike repositories, domains, and development environment extensions. In at least one documented case, a fake extension installed a legitimate remote access tool configured to connect to attacker infrastructure.
Execution, Persistence, and Lateral Movement
Control of an OpenClaw instance provides attackers with an automation framework capable of executing shell commands, reading and modifying files, and interacting with external services through trusted APIs.
Persistence can be achieved by modifying agent configuration files, stored memory, or scheduled workflows, allowing activity to survive restarts. In some cases, attackers could embed recurring tasks that performed data exfiltration or system interaction without further command input.
Harvested credentials enabled lateral movement into cloud environments and enterprise SaaS platforms, often without additional interaction with the original host. This expanded the impact from a single compromised system to multiple environments connected through the agent.
Enterprise Risk Implications
OpenClaw deployments were frequently observed outside formal IT approval processes, introducing shadow AI risk into enterprise environments. Because the agent operates using legitimate credentials and sanctioned APIs, its activity can bypass traditional perimeter defenses and data loss prevention controls.
From a defensive standpoint, this activity can resemble insider threat behavior, even though it results from external compromise or misconfiguration rather than malicious employees.
Risk Reduction and Operational Guidance
The risks associated with OpenClaw are primarily operational and architectural in nature. Effective mitigation focuses on limiting exposure and reducing impact rather than eliminating risk entirely.
Preventive Measures:
- Control UI Isolation: Bind the Control UI and Gateway to localhost only.
- Network Exposure Control: Do not expose OpenClaw services directly to the public internet.
- Privilege Reduction: Run OpenClaw as a non-root user with minimal OS permissions.
- Credential Scope Control: Use least-privilege tokens for all integrations.
- Tool Restrictions: Disable shell execution, file write access, and browser automation unless strictly required.
- Skill Allowlisting: Install only vetted and reviewed skills from trusted sources.
- Secret Hygiene: Rotate and revoke credentials following any suspected exposure.
- Monitoring: Log execution events, configuration changes, and outbound connections.
Additional guidance is available in OpenClaw’s published security documentation.
Assessment
OpenClaw introduces a high-impact attack surface when deployed without strict controls. The observed risks are consistent with prior incidents involving automation frameworks and orchestration tools, where privilege aggregation and trust assumptions, rather than software flaws, enabled compromise.
Organizations evaluating OpenClaw should treat it as privileged infrastructure, subject to the same security, monitoring, and isolation requirements as production control systems.




