Exploiting Mapbox API Tokens: Unauthorized Usage & Billing Abuse
Mapbox is a powerful mapping platform that offers customizable maps, geocoding, and location-based services through its APIs and SDKs. However, when API tokens lack proper URL restrictions, they become a prime target for abuse. In this research, we
Hello Researchers,
I'm Mahesh, also known as "hackruler", a Security Researcher at Jsmon. Our team focuses on identifying and exploiting various API key vulnerabilities. In this blog, we dive into the unauthorized usage and potential billing abuse of Mapbox API Tokens—a crucial security concern for developers.
Mapbox is a powerful mapping platform that offers customizable maps, geocoding, and location-based services through its APIs and SDKs. However, when API tokens lack proper URL restrictions, they become a prime target for abuse. In this research, we demonstrate how an exposed Mapbox API key can be exploited, leading to unauthorized access and potential financial loss.
Let’s uncover the risks and learn how to secure API keys effectively! 🚀
Mapbox Token
-
Mapbox Provides a default token which is being created while you signin to mapbox.
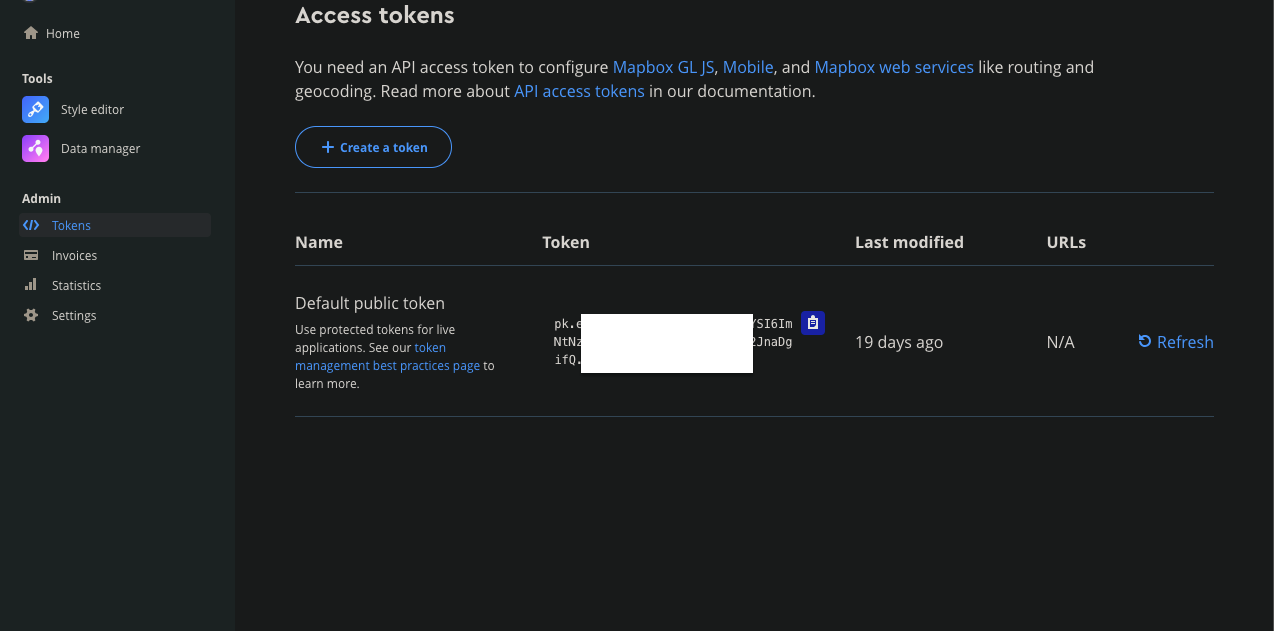
This token is used for testing in your website for testing purpose.
-
You can create more tokens to use mapbox services.

After creating token you can use this token in your application.
URL Restriction in Mapbox
When you are creating Mapbox api token. Mapbox provides a URL restriction feature that can be used by admin to use only in their hosts.
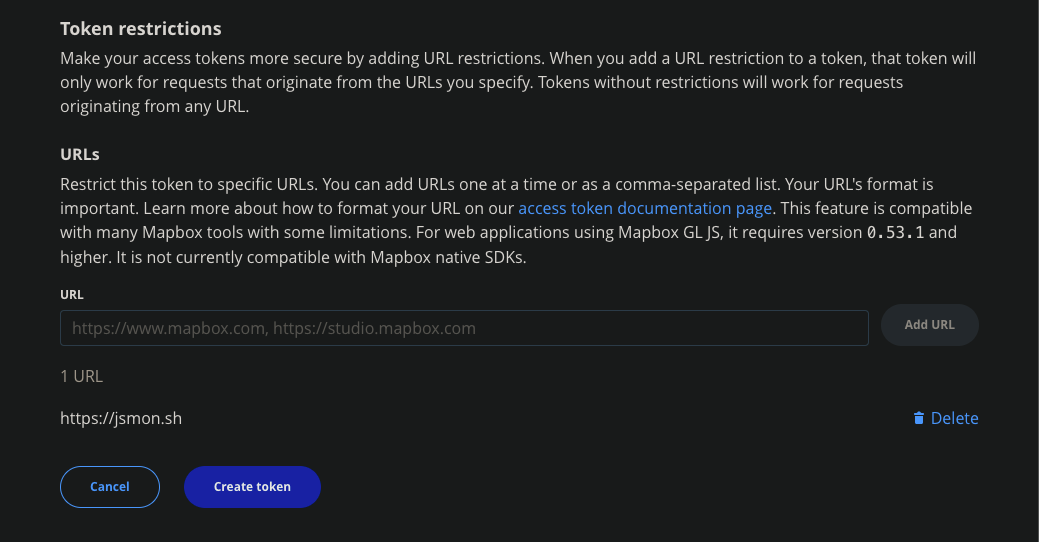
What if the admin do not set the URL restriction??
Mapbox provides free usage of api token for a number of request for every type of service.
You can have a look at this to check for Mapbox billing details.
If the Admin doesn't set the URL Restriction, an Attacker can abuse the API to increase the billing for the Organization which causes financial loss to the Organization.
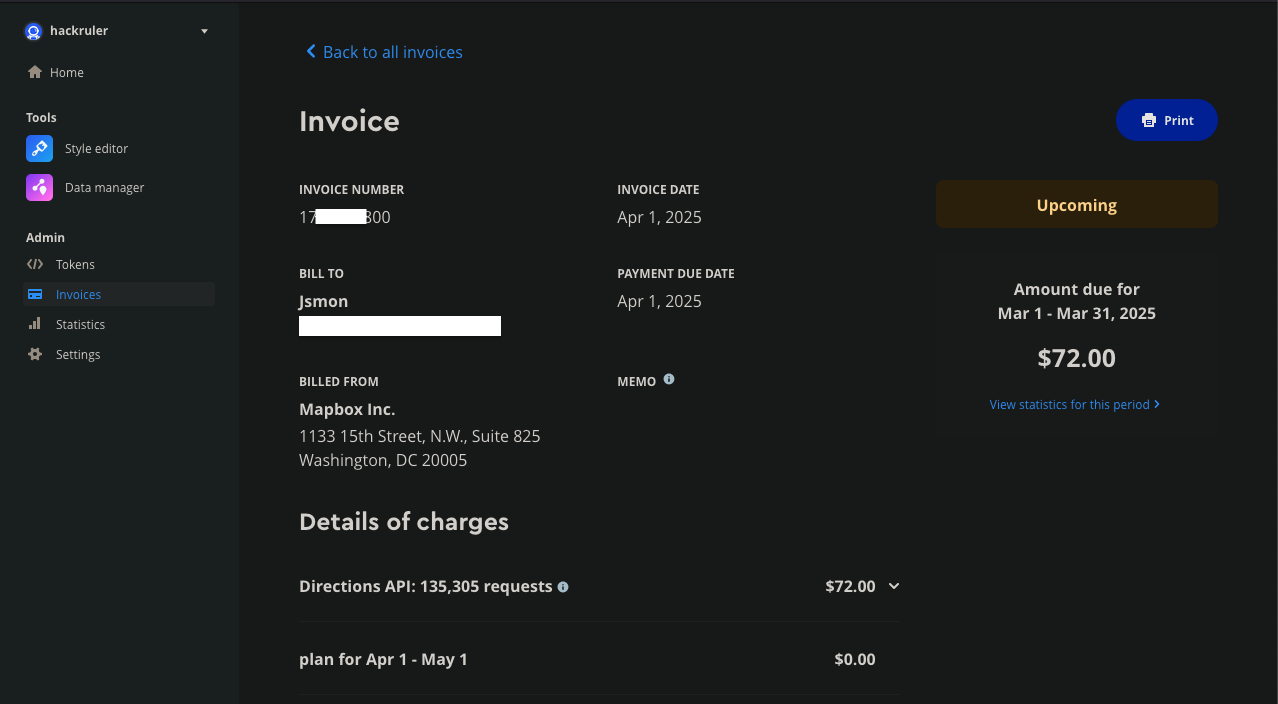
We have tried to hit the number of request more than free tier, so that we can see how much bill an attacker can create for an organization.
Here are some screenshots we used for testing the API for abuse.
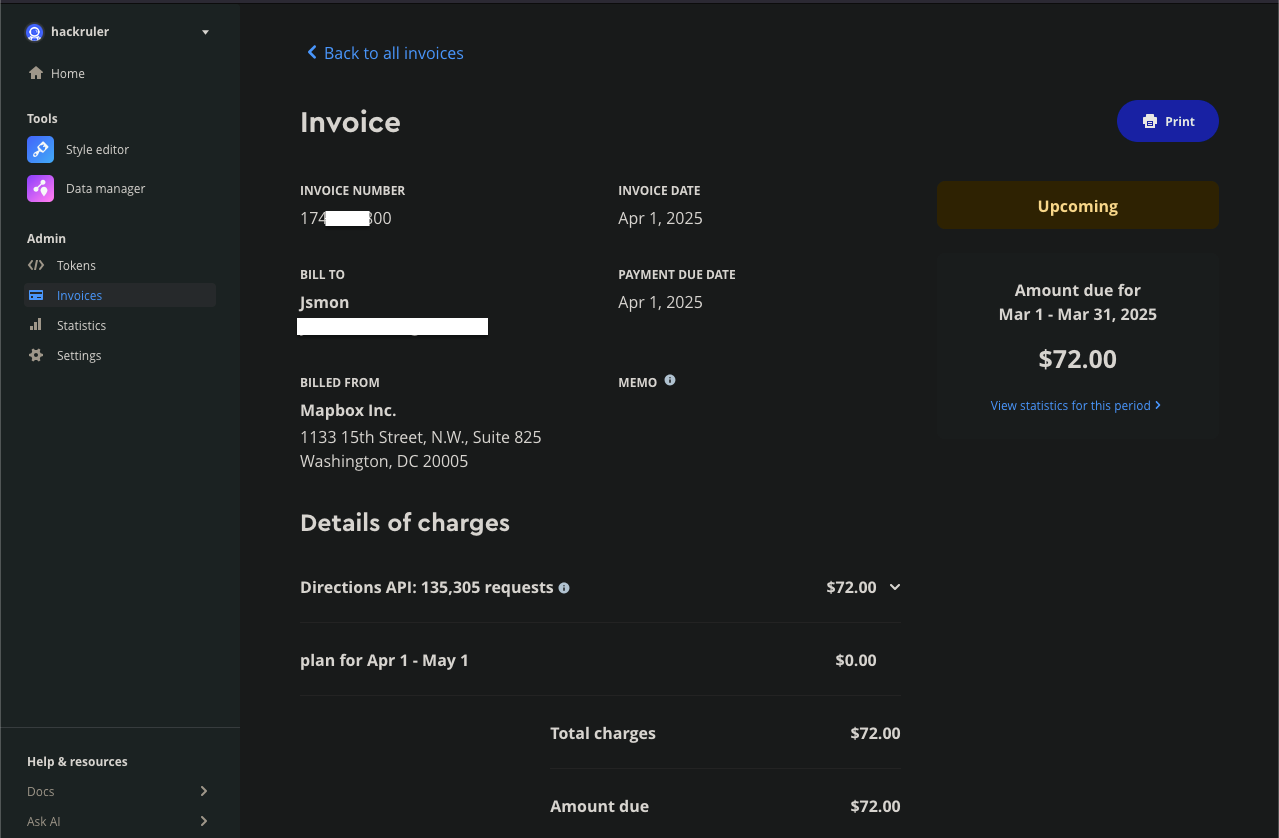
** This bill is created in a few hours of hitting the request using the api token.
So an attacker can create a way higher bill than this in a month.
How URL restriction works ??
To show this, we have hosted a website to show that api abuse and unathenticated billing can be stopped.
We have hosted a map and include a public token with No URL restriction.
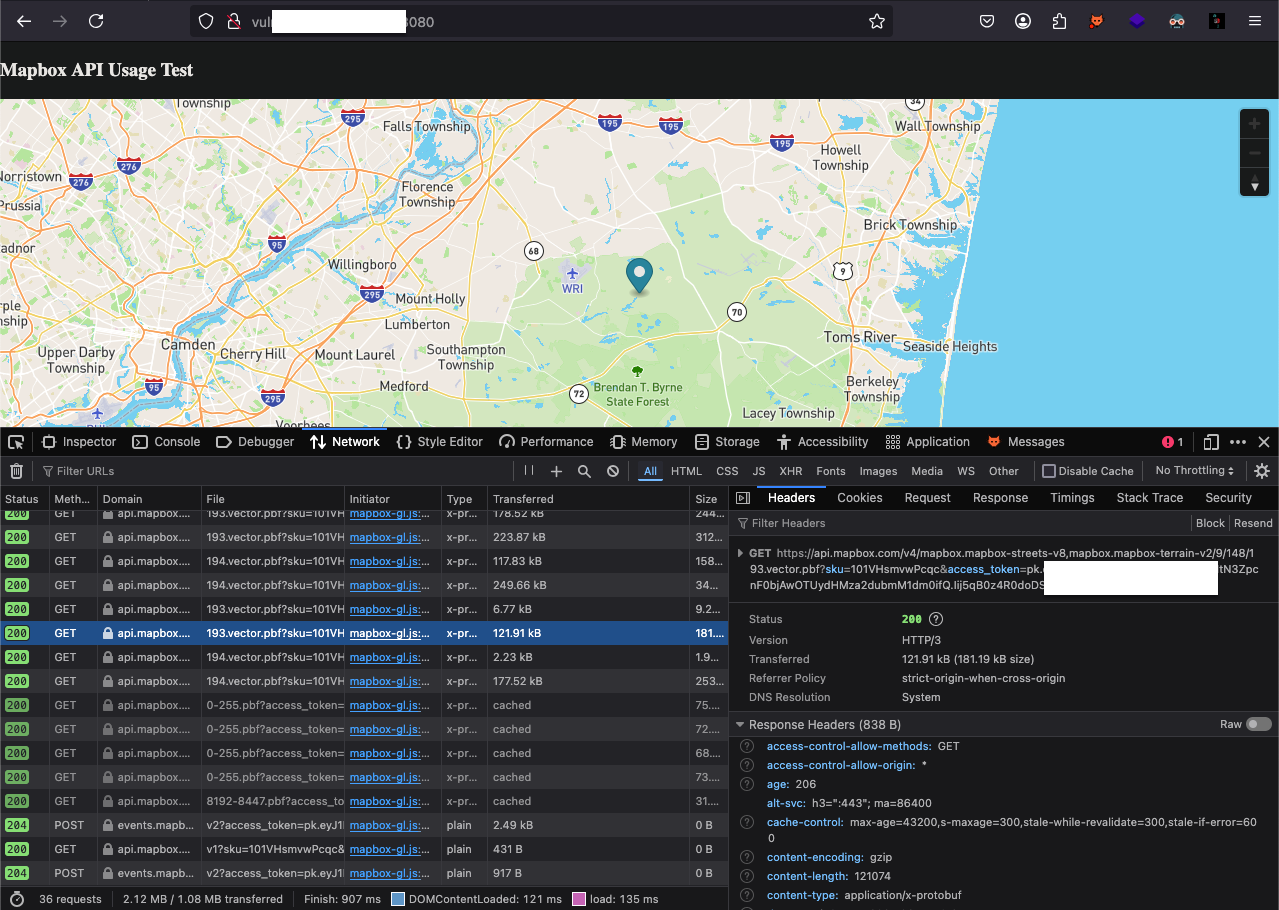
Came to see that all the request to mapbox api using that api token is giving us 200 ok response.
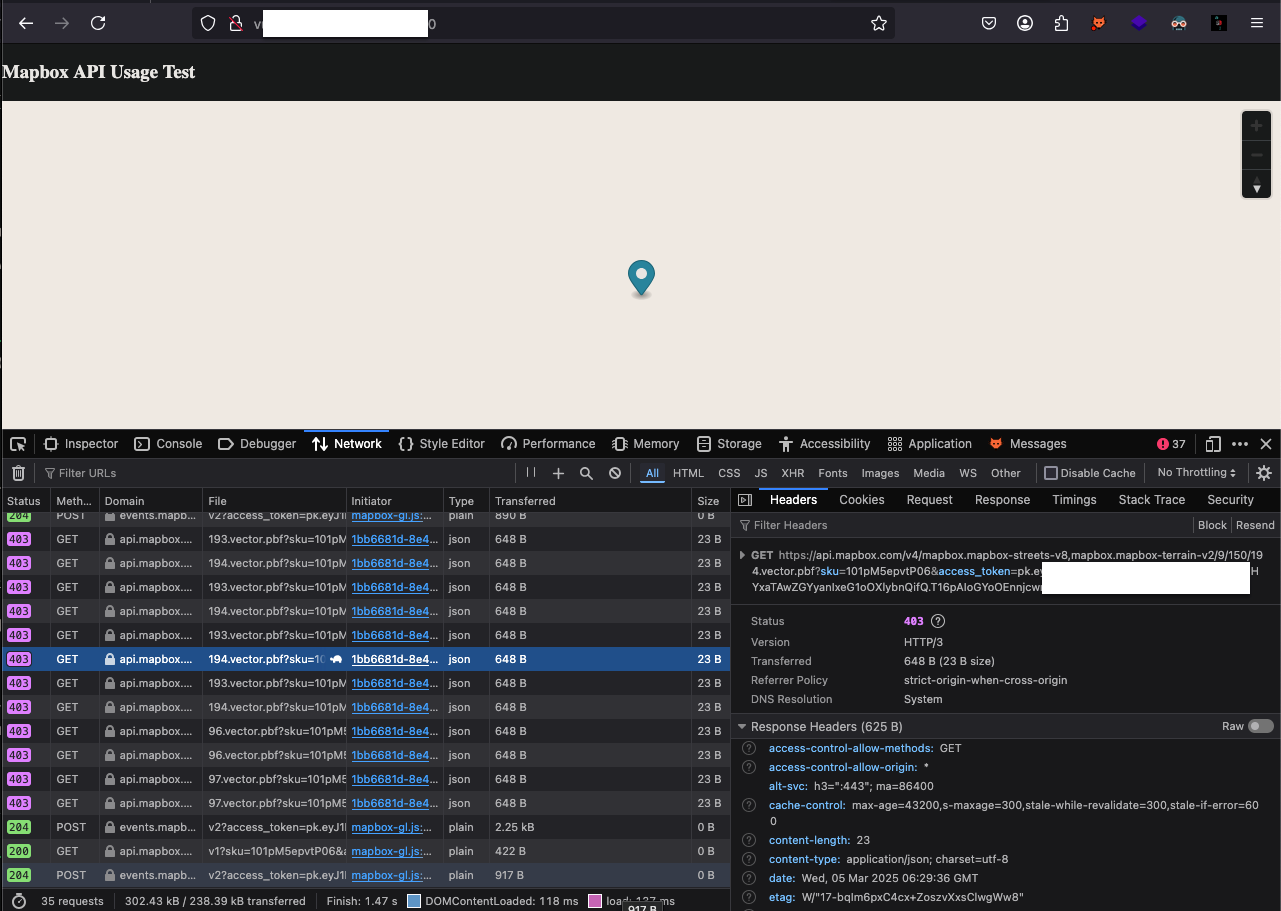
When we have used a URL restricted API Token, we got 403 response as the API calls are originating from a different domain.
How can you find mapbox API key ??
You can find the Mapbox API keys using the regex \b[ps]k\.eyJ[a-zA-Z0-9]+\.[a-zA-Z0-9-_]+\b
You can search this API Key in JS files, Source Code......
How to Find via Jsmon ??
- Upload the js files to Jsmon via file scan, url scan or domain scan.
- Mapbox API keys would be visible in Keys & Secrets section.
Remediation
-
Mapbox provides URL restriction feature that will restrict the use of API key used by any other application. It gives 403 response code if the call is coming from any other host.
-
Instead of exposing the Mapbox API key in the frontend, create a middleware API that:
- Accepts requests from your legit users (authenticated or verified).
- Validates requests (e.g., rate limiting, user sessions, IP restrictions).
- Forwards only legitimate requests to Mapbox using the API key.
- Hides the API key from the client completely.
Conclusion
If the URL restriction is not being set properly for the API token. An attacker can abuse the API Key and this can lead to unauthorized billing.
How We Can Help?
In 2026, Security tooling must deliver context—not just alerts. Jsmon continuously maps and monitors your JavaScript and web attack surface, identifying real risks like exposed endpoints, leaked secrets, misconfigurations, and client-side vulnerabilities as they emerge.
By combining context-aware analysis with continuous monitoring, Jsmon dramatically reduces false positives and helps teams focus on issues that are actually exploitable.
Secure your attack surface in real time with Jsmon.
Thanks,
Mahesh
Security Researcher, Jsmon