JavaScript Console Warnings That May Reveal a Security Breach
The browser console is an integrated developer tool found in most modern web browsers, such as Chrome, Firefox, and Safari. It enables developers to monitor and interact with different elements of a webpage, including errors, warnings, logs, and network activity.
Introduction:
The browser console is an integrated developer tool found in most modern web browsers, such as Chrome, Firefox, and Safari. It enables developers to monitor and interact with different elements of a webpage, including errors, warnings, logs, and network activity. Additionally, it offers a JavaScript runtime environment, making it a valuable resource for testing and debugging code.
Modern browsers are equipped with security and debugging features that help developers identify potential issues through console warnings. Some of these warnings include; CSP (Content Security Policy) Violations, Cross-Origin Request Warnings, Memory Leaks, Slow Script Warnings and many more.
Some console warnings aren’t just harmless alerts - they can hint at real security issues. Things like blocked scripts, CSP violations, or cross-origin errors might mean there’s a vulnerability or even an attack happening behind the scenes. Keeping an eye on these warnings can help catch problems early. In this blog, we will discuss further on how to assess these warnings and take immediate action.
Why do they matter for Security?
Console warnings aren’t just for debugging - they can be your first sign that something’s not right. Browsers often flag things like unsafe scripts, blocked resources, or suspicious cross-origin requests, which could point to real security risks like XSS or misconfigurations. Paying attention to these messages helps you catch problems early, before they turn into serious threats. It’s a simple habit that can make a big difference in keeping your site safe.
Critical Console Warnings to Look For
Now comes the important part, where we’ll look at console warnings - along with examples - that could indicate a security breach, or even help prevent one.
1. Mixed Content
Warning: Mixed Content: The page at 'https://example.com' was loaded over HTTPS, but requested an insecure script 'http://othersite.com/script.js'. This request has been blocked.
This warning means that a web page using HTTPS is trying to load some assets (like images, scripts, or stylesheets) over HTTP instead of HTTPS. When a site is loaded over HTTPS (secure), all its content should also come from secure (HTTPS) sources. If any part of the page uses HTTP, it's called mixed content, because part of the page is secure and part is not.

This typically occurs when:-
- A JavaScript AJAX/fetch call is made to
http://...instead ofhttps://... - A
<script>,<img>,<iframe>, or<link>tag uses a URL starting withhttp://on anhttps://page.
Security Indications: Attackers can intercept HTTP resources in transit and inject malicious code (e.g., MITM attack). This is especially critical if the page loads JavaScript over HTTP.
Some other attacks it can cause include Man-in-the-Middle (MITM) attacks, eavesdropping, Content Security Policy (CSP) bypass, downgrade attacks.
Bug Bounty POV: Report as “mixed content vulnerability” if it allows tampering or reflects insecure design.
2. CORS Policy Errors
Warning: Access to fetch at 'https://target.com/api' from origin 'https://xyz.com' has been blocked by CORS policy
This happens when a website (https://yoursite.com) tries to make a request to another domain (https://target.com) - and the target server does not allow it.
The browser blocks the request for security reasons, unless the response from https://target.com/api includes the proper CORS header.
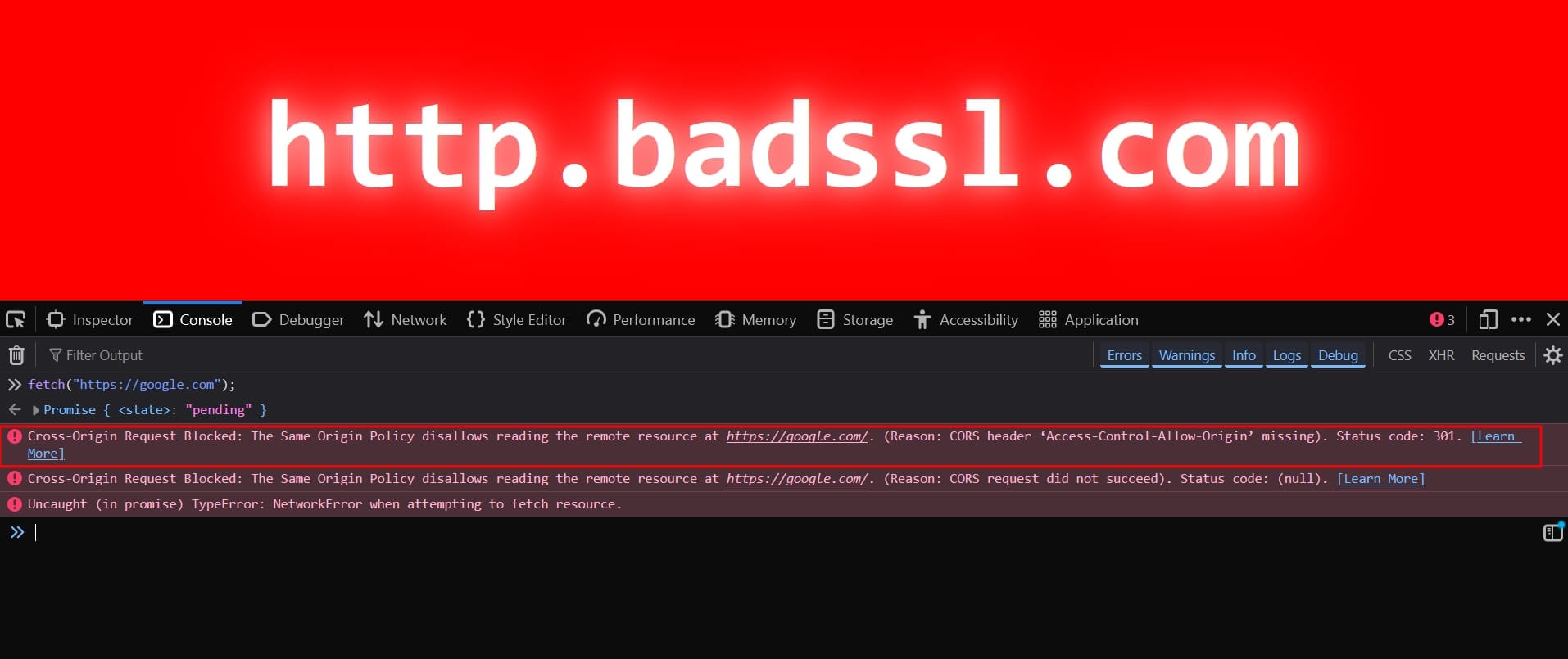
Security Indications: Improperly configured CORS can either:
- Leak sensitive data to malicious origins.
- Allow privilege escalation via token sharing.
Bug Bounty POV: If you find CORS misconfigurations (e.g., wildcard * with credentials), that’s gold.
3. Permissions Policy Violations
Warning: Permissions-Policy header is not set. Features like ‘camera’, ‘microphone’, and ‘geolocation’ might be accessible by iframes.
This typically happens when the website fails to set a restrictive Permissions-Policy (formerly 'Feature-Policy'), allowing access to APIs.
Security Indications: Malicious iframes or subdomains could misuse these APIs (e.g., background camera access).
Bug Bounty POV: Insecure or missing Permissions-Policy headers can be a reportable misconfiguration on HackerOne and Bugcrowd if they lead to a demonstrable security impact.
4. SameSite Cookie Misconfiguration
Warning: A cookie associated with a cross-site resource at https://example.com was set without the `SameSite` attribute. It has been blocked.
The cookie lacks a 'SameSite' attribute or is using an unsafe value like None without Secure.
Security Indications: This can enable Cross-Site Request Forgery (CSRF) attacks by leaking session cookies in cross-site requests.
Bug Bounty POV: Cookies without SameSite+Secure are often a reportable issue in login flows or sensitive endpoints.
Tools to Detect and Monitor These Warnings
To stay ahead of potential breaches, developers should integrate monitoring tools into their workflow. Here are some recommended options:
- Browser DevTools: Your first line of defense for real-time warnings.
- Sentry: Tracks JavaScript errors and unusual user behavior.
- Report URI: Collects CSP, CORS, and other browser security reports.
Conclusion:
Console warnings are often ignored during development - but they can offer vital clues about active or upcoming security threats. Recognizing them as early warning signs gives developers a powerful edge. By combining vigilance with the right tools and secure coding practices, you can transform your console from a debug tool into a security sensor.
How We Can Help?
In 2026, security teams need context—not just alerts. Jsmon continuously discovers and monitors your application attack surface, identifying real risks such as exposed endpoints, leaked secrets, misconfigurations, and sensitive data exposure as they appear.
By combining context-aware analysis with continuous monitoring, Jsmon reduces false positives and helps teams focus only on issues that are truly exploitable.
Secure your applications in real time with Jsmon.