Uncover Hidden URLs with Archived JavaScript Files: A Bug Bounty Recon Trick
When hunting for vulnerabilities or hidden endpoints in web applications, archived JavaScript files can be a goldmine. These scripts often contain forgotten or deprecated URLs, API endpoints, and internal services that might still be alive but are no longer linked from the main website. In this post, we’ll walk through a simple and effective way to extract URLs from archived JavaScript files using publicly available tools.
This method leverages passive reconnaissance techniques—no brute-force, no scanning—just clever use of archives and automation to extract potentially sensitive URLs. Let’s dive in.
🔍 Step 1: Get All Archived URLs Using Passive Sources
echo jsmon.sh | waybackurls | sort -u | tee wayback.txt
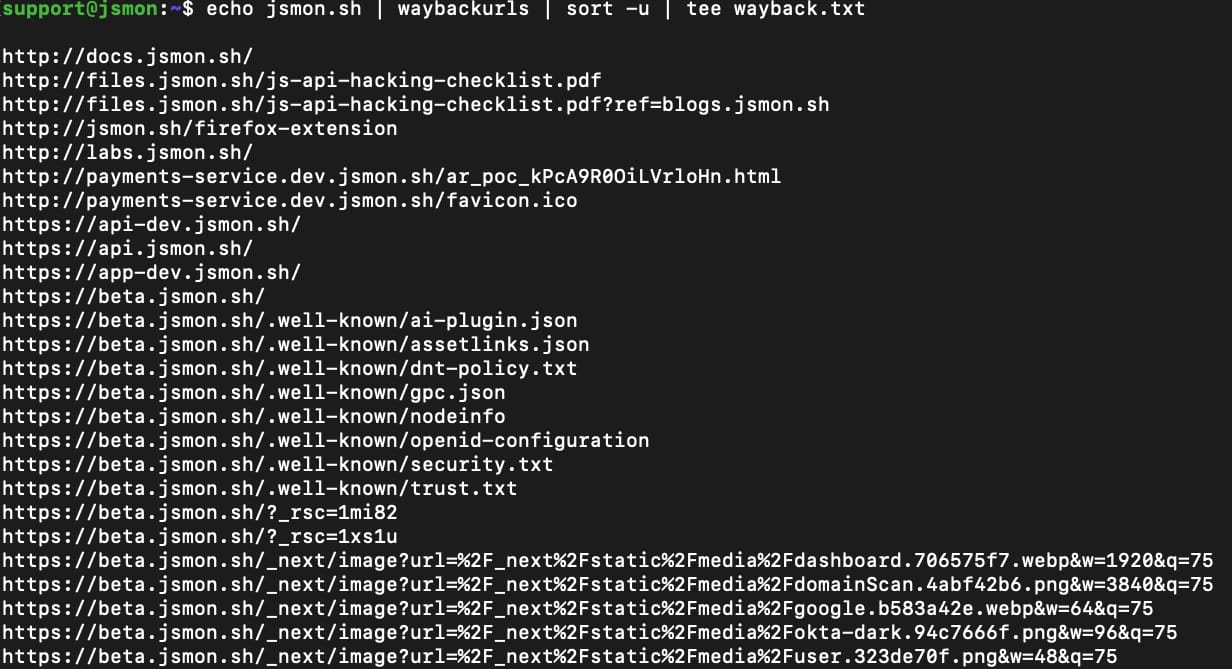
This will fetch URLs from sources like the Wayback Machine and save them in wayback.txt.
📁 Step 2: Filter JavaScript Files from the Archived URLs
Now, extract only the JavaScript file URLs from the full list.
cat wayback.txt | grep -E '\.js$|\.js\?' | tee jsurls.txt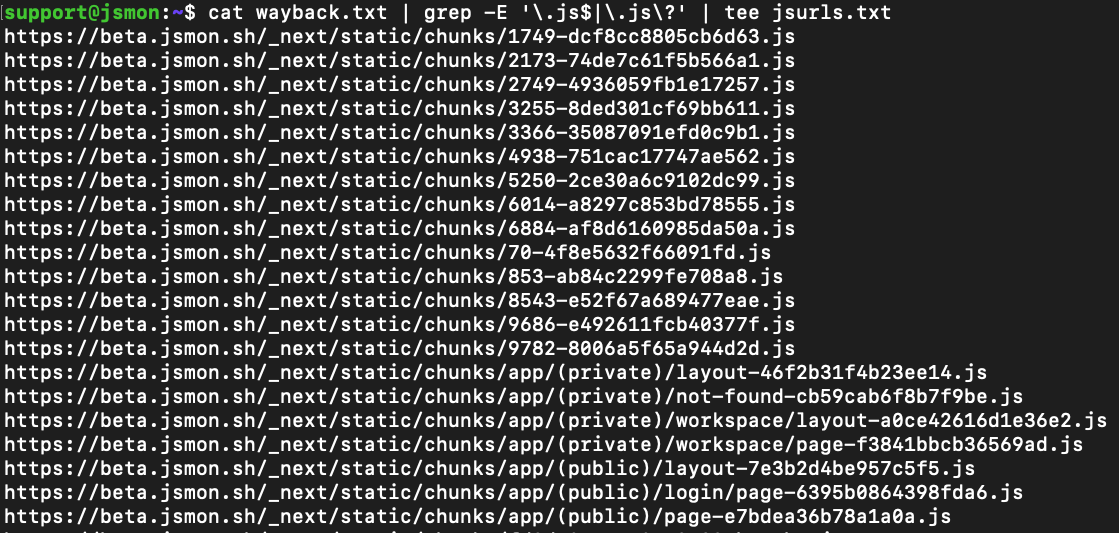
This filters out anything that doesn’t look like a .js file or query-based JS endpoint.
🌐 Step 3: Check for Live JavaScript Files Using httpx
Create a directory to store the responses, and then use httpx to fetch only the live JavaScript files (i.e., returning HTTP 200).
mkdir res; cat jsurls.txt | httpx -mc 200 -srd res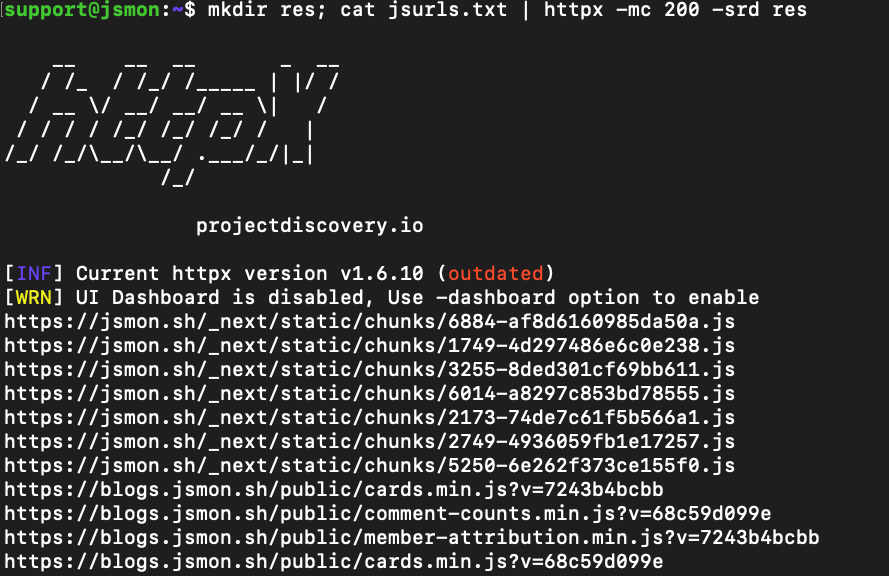
Each live JS file response will be saved in the res folder for further inspection.
🔗 Step 4: Extract All URLs from JavaScript Content
Use grep to find all hardcoded URLs inside the JS responses.
cat res/* | grep -Eo 'https?://[a-zA-Z0-9._~:/?#@!$&'\''()*+,;=%-]+' | sort -u | tee urls.txt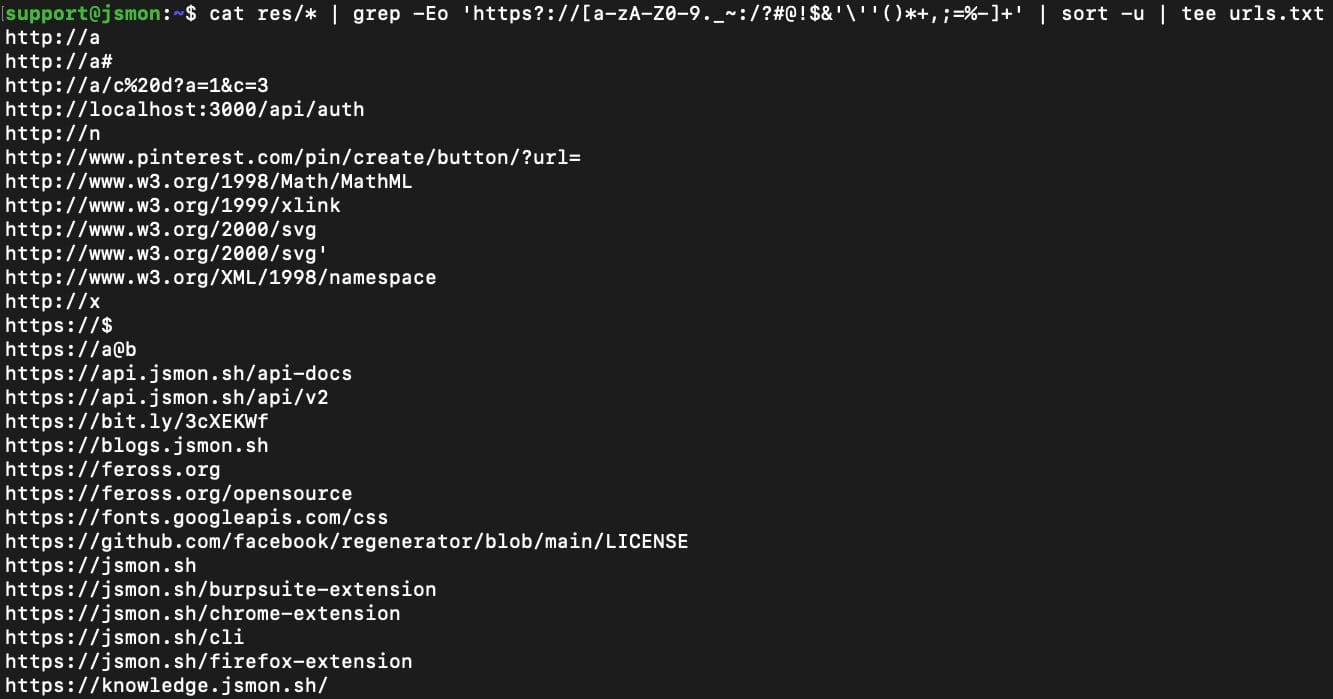
These URLs can lead to admin panels, hidden APIs, third-party integrations, and more—all of which could be potential entry points for further recon or exploitation.
Conclusion
This passive recon technique is especially useful in the early stages of a bug bounty program or red team assessment. By digging into historical JavaScript files, you may uncover deprecated but still-active URLs, internal APIs, or forgotten services that developers never meant to expose.
Keep exploring, automate smartly, and never underestimate the value of archived data.
Would you like a downloadable script or cheatsheet version of this workflow?
👉 Click here to download the bash script.
👉 Visit Jsmon for JS security at scale.
Thanks for reading!