Extract Hidden JS URLs using Katana
When mapping out the attack surface of an application, JS files often contain a wealth of valuable information, API endpoints, keys, hidden paths, and more. One powerful tool that helps automate the discovery of these files is Katana, a fast and extensible web crawling framework by ProjectDiscovery.
When performing reconnaissance or mapping out the attack surface of a web application, JavaScript files often contain a wealth of valuable information, API endpoints, keys, comments, hidden paths, and more. One powerful tool that helps automate the discovery of these files is Katana, a fast and extensible web crawling framework by ProjectDiscovery.
In this blog post, we’ll walk through how to use Katana to efficiently enumerate JavaScript files from a target website.
What is Katana?
Katana is a next-generation web crawler written in Go that supports modern crawling features like:
- Headless crawling
- URL extraction from JavaScript
- Support for custom scripts
- Flexible filters
- Integration with other tools in your pipeline
It’s designed for both offensive and defensive security professionals who need fast, scriptable web reconnaissance.
Installation
You can install Katana using go install:
go install github.com/projectdiscovery/katana/cmd/katana@latest
Make sure $GOPATH/bin is in your system’s $PATH.
You can also download prebuilt binaries from the official GitHub repository.
Basic Usage to Enumerate JavaScript Files
To crawl and extract URLs from a target website, you can use the following command:
katana -u <https://youtube.com> -jc
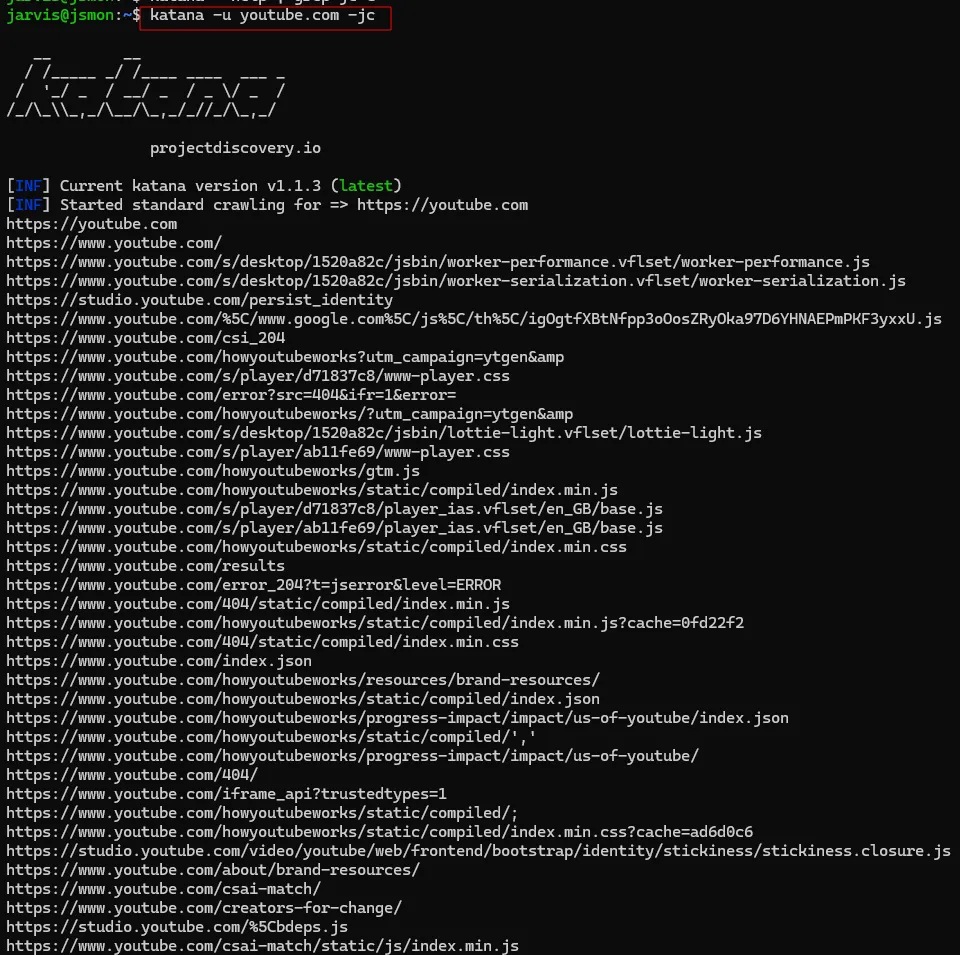
Breakdown:
-u: Specifies the target URL-jc: Enables JavaScript crawling and file extraction
This will output all discovered URLs including .js files. To filter only the JavaScript files, you can use grep:
katana -u <https://youtube.com> -jc| grep -E '\.js$|\.js\?'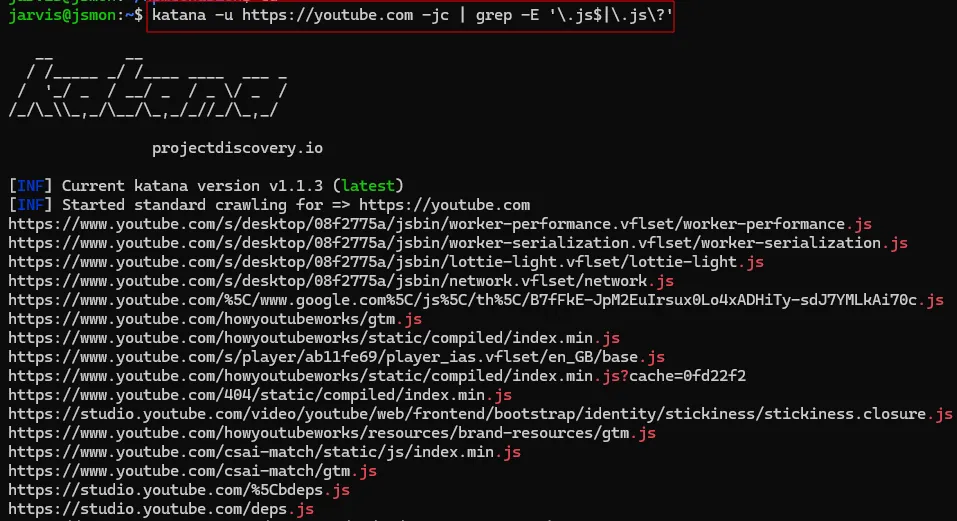
Advanced Tips
Enable jsluice parsing in javascript file
katana -u <https://youtube.com> -jc -jsl
Enable crawling of known files
katana -u <https://youtube.com> -jc -kf all
Crawl with depth control:
katana -u <https://youtube.com> -jc -d 5
Use with concurrency for faster results:
katana -u <https://youtube.com> -jc -c 20
Final Thoughts
Katana is a powerful and flexible crawler that makes JavaScript file enumeration fast and easy. With just a few flags, you can uncover potentially sensitive files that may expose valuable insight into the target's backend or APIs. Integrating Katana into your recon workflow will save time and significantly boost your bug bounty or pentest efforts.
Visit jsmon.sh for automated JS URL extraction, javascript analysis and monitoring at scale.
Thanks for reading!