attack surface
How Subdomains Become Attack Vectors
A Deep Dive into Enterprise Deployments, DevOps Reality, and External Attack Surfaces. Subdomains - most consistently exploited attack surfaces.

attack surface
A Deep Dive into Enterprise Deployments, DevOps Reality, and External Attack Surfaces. Subdomains - most consistently exploited attack surfaces.

Security researchers and bug hunters, the game just changed. We are thrilled to announce the latest version of the Jsmon Burpsuite Extension. In previous versions, the extension acted primarily as a bridge, you could configure settings and send URLs to Jsmon, but you had to switch back to the Jsmon

supply chain attack
This report provides a detailed analysis of a major, campaign attack that unfolded on 15 September 2025. One campaign, known as the "Shai-Halud attack," compromised packages belonging to cybersecurity firm CrowdStrike, targeting their internal CI/CD pipelines.

bug bounty
Amazon S3 bucket takeovers are a common and impactful vulnerability in web applications. When a JavaScript file references an S3 bucket that no longer exists (but is still expected to serve assets), attackers can claim ownership of that bucket and serve malicious content in its place.
dependency confusion
A Dependency Confusion attack, also known as a substitution attack, occurs when a malicious actor uploads a package with the same name as an internal or private dependency to a public package registry. If the development

second order domain takeover
Second-order domain takeovers target forgotten domains still referenced in live JavaScript files. This overlooked threat can lead to serious security risks. Learn how to detect them manually—or automate the entire process with jsmon.sh.

bugbounty
When hunting for vulnerabilities or hidden endpoints in web applications, archived JavaScript files can be a goldmine. These scripts often contain forgotten or deprecated URLs, API endpoints, and internal services that might still be alive but are no longer linked from the main website. In this post, we’ll walk
katana
When mapping out the attack surface of an application, JS files often contain a wealth of valuable information, API endpoints, keys, hidden paths, and more. One powerful tool that helps automate the discovery of these files is Katana, a fast and extensible web crawling framework by ProjectDiscovery.

bugbounty
When performing reconnaissance or source code reviews, JavaScript files are a goldmine of leaked credentials, secrets, tokens, and other sensitive artifacts. This blog post is a curated resource library of 100 regex patterns designed to help security researchers and engineers.
bugbounty
APIs are the backbone of modern applications, but they often leak sensitive information through JavaScript files, misconfigurations, and weak security measures. This checklist focuses on API hacking techniques, with special attention to JavaScript file analysis.
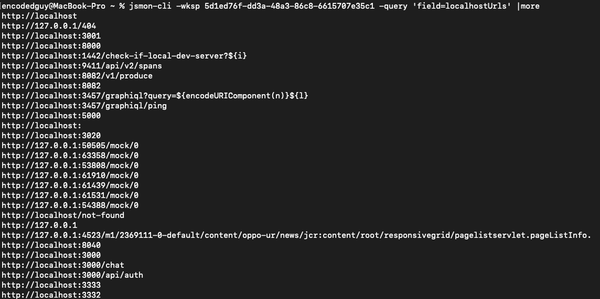
bugbounty
jsmon-cli is a fast and convenient tool (API client) for your JS hacking powered by jsmon.sh. jsmon.sh is a JS security framework made for security enthusiasts, bugbounty hunters, penetration testers
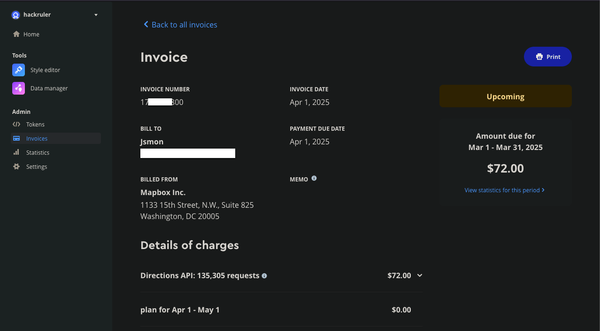
bug bounty
Mapbox is a powerful mapping platform that offers customizable maps, geocoding, and location-based services through its APIs and SDKs. However, when API tokens lack proper URL restrictions, they become a prime target for abuse. In this research, we