5 Fast Subdomain Discovery Tools Every Hacker Needs
Subdomain enumeration is a very important tactic in bugbounty or in general cybersecurity research. It helps you to uncover hidden attack surface. In this blog, we'll dive into top 5 subdomain enumeration or discovery tools that every hackers almost uses.

Why Subdomain Enumeration is Critical for Bug Bounty Success
Finding subdomains is like discovering hidden doors in a massive building. While everyone's banging on the main entrance, you're quietly slipping through side entrances that most people don't even know exist.
In bug bounty hunting, subdomains often house the most valuable targets. Development servers, staging environments, forgotten admin panels, and legacy applications all love to hide behind obscure subdomains. These forgotten corners of the internet frequently contain the juiciest vulnerabilities and the biggest payouts.
The problem? Manual subdomain discovery is painfully slow. You need tools that can scan thousands of possibilities in minutes, not hours. That's where these five powerhouse tools come in.
Tool #1: Subfinder - Lightning Fast and Super Easy
Subfinder is like having a really smart assistant that can check hundreds of places at once. Built by ProjectDiscovery, this tool finds subdomains incredibly fast without breaking a sweat.
What makes Subfinder special is its massive collection of data sources. It queries over 30 different APIs and services simultaneously, including Certificate Transparency logs, DNS databases, and search engines. The result? Comprehensive subdomain lists in record time.
Installation:
go install -v github.com/projectdiscovery/subfinder/v2/cmd/subfinder@latest
Basic Usage:
subfinder -d target.com -o subdomains.txt
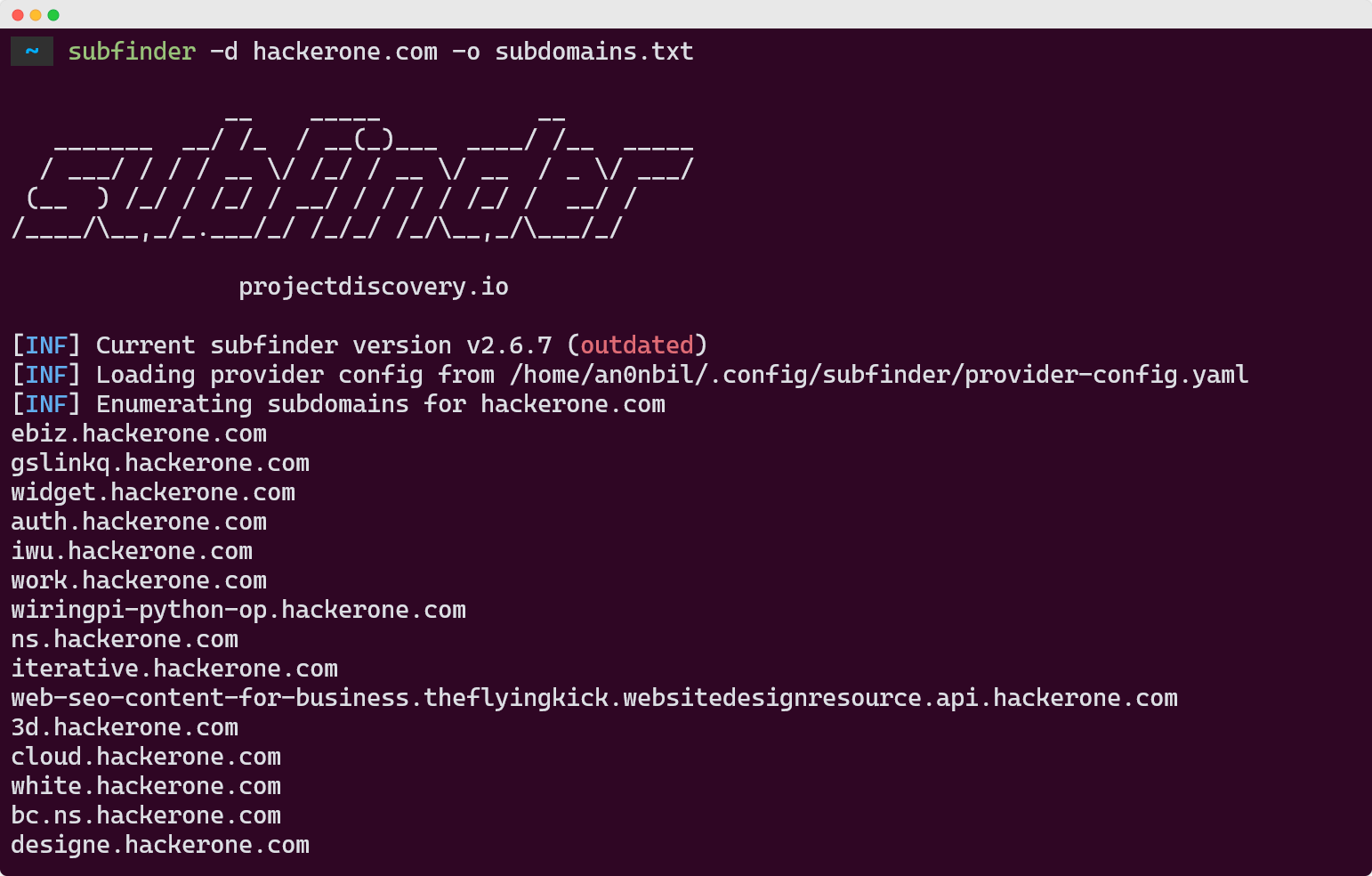
Pro Tip: Configure API keys for sources like Shodan, VirusTotal, and SecurityTrails to unlock Subfinder's full potential. The difference in results is night and day.
Subfinder excels at finding subdomains without sending a single packet to your target. This makes it perfect for reconnaissance phases where you want to stay completely under the radar. Visit Subfinder's documentation for more features.
Tool #2: Amass - The Complete Information Gatherer
If Subfinder is like a smart assistant, Amass is like having a private detective. This tool doesn't just find subdomains but builds complete maps of your target's online presence.
Developed by OWASP, Amass combines passive reconnaissance with active DNS enumeration. It can correlate data from dozens of sources to paint a complete picture of your target's infrastructure.
Installation:
sudo apt install amass
Passive Enumeration:
amass enum -passive -d target.com -o amass_results.txtActive Enumeration:
amass enum -active -d target.com -brute -w wordlist.txt -o amass_active.txt
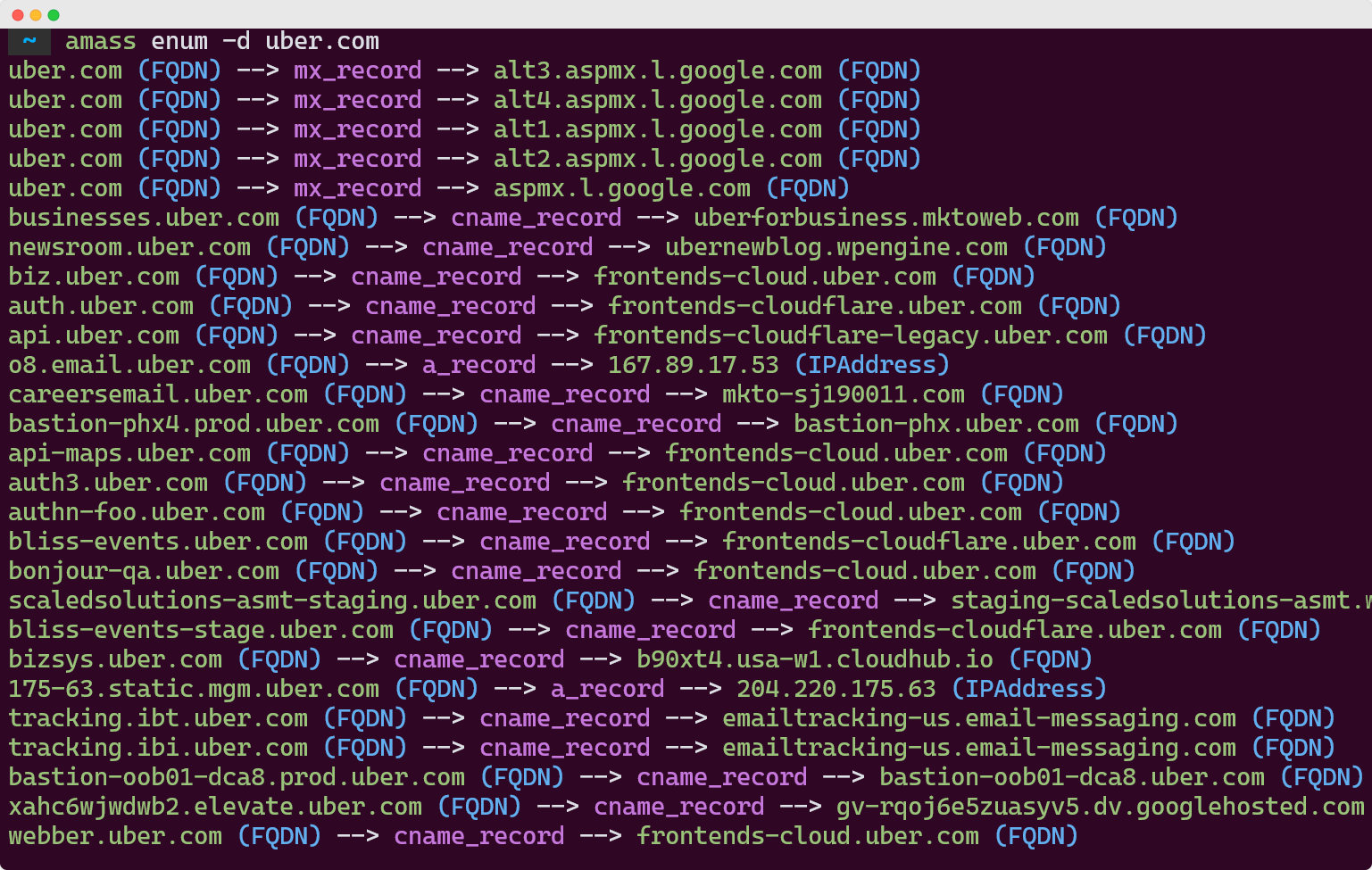
Amass shines when you need deep intelligence gathering. Its database feature lets you store and track changes in your target's infrastructure over time. The tool's visualization capabilities are also impressive. You can generate network graphs showing relationships between domains, subdomains, and IP addresses. See Amass docs for more features.
Tool #3: Assetfinder - Simple and Gets the Job Done
Sometimes you don't need something complicated when a simple tool works perfectly. Assetfinder is exactly that - straightforward, fast, and really effective.
Created by Tom Hudson, Assetfinder focuses on speed and simplicity. It queries a handful of reliable sources and returns results in seconds. No complex configuration, no overwhelming options - just point and shoot.
Installation:
go get -u github.com/tomnomnom/assetfinder
Usage:
assetfinder target.com
Find Subdomains for Multiple Domains:
cat domains.txt | assetfinder
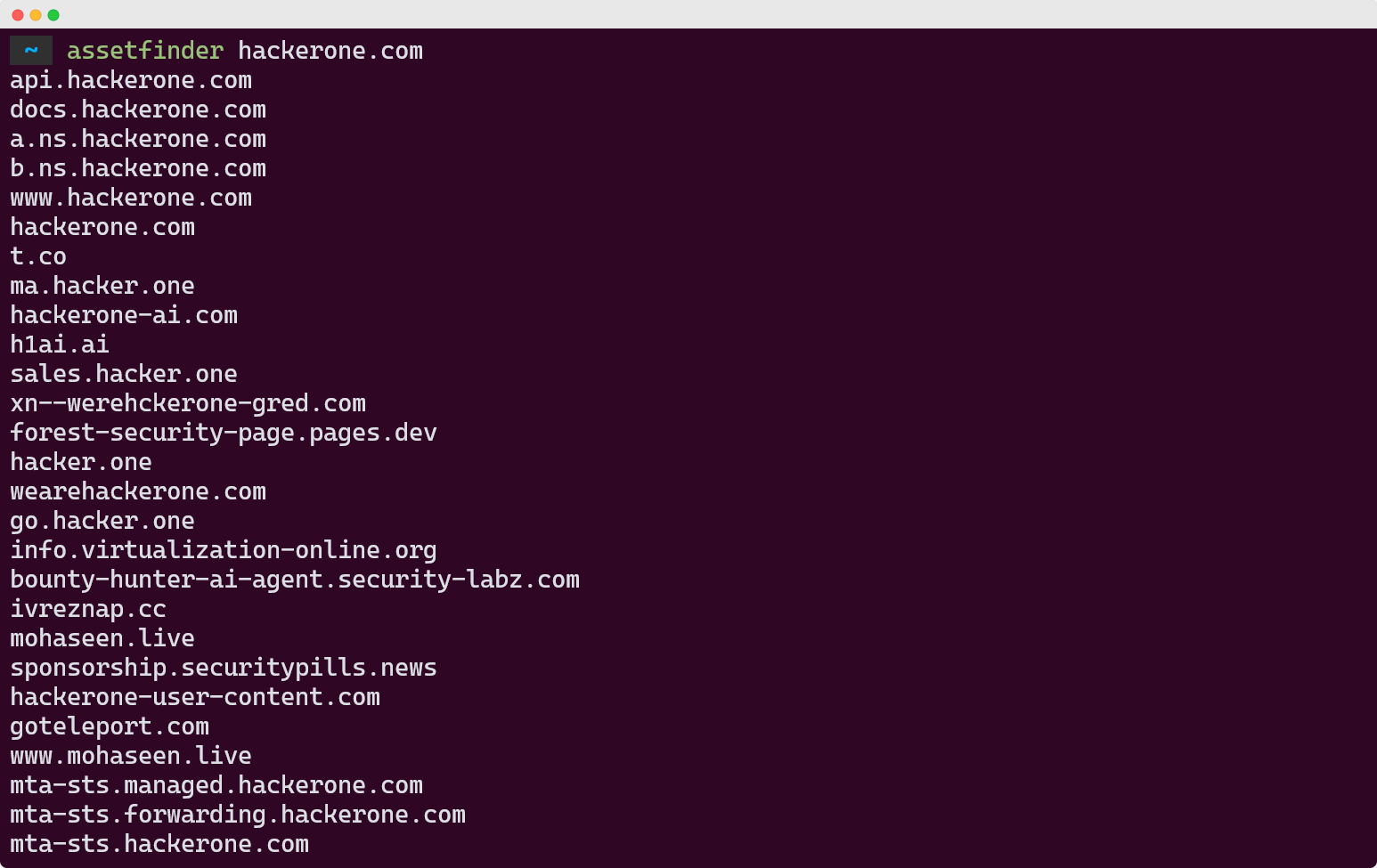
Assetfinder is perfect for quick reconnaissance when you're testing multiple targets. Its lightweight design means you can run it on VPS instances with minimal resources. The tool also plays nicely with shell pipes, making it easy to chain with other tools.
Tool #4: Sublist3r - The Reliable Old Friend
Sublist3r might be older than some of the other tools here, but it's still incredibly dependable. Think of it as that reliable friend who always comes through when you need them.
This Python-based tool queries multiple search engines and services, including Google, Yahoo, Bing, Baidu, and Ask. It also integrates with subbrute for additional brute force capabilities.
Installation:
sudo apt install sublist3r
Basic Usage:
sublist3r -d target.com -o results.txt
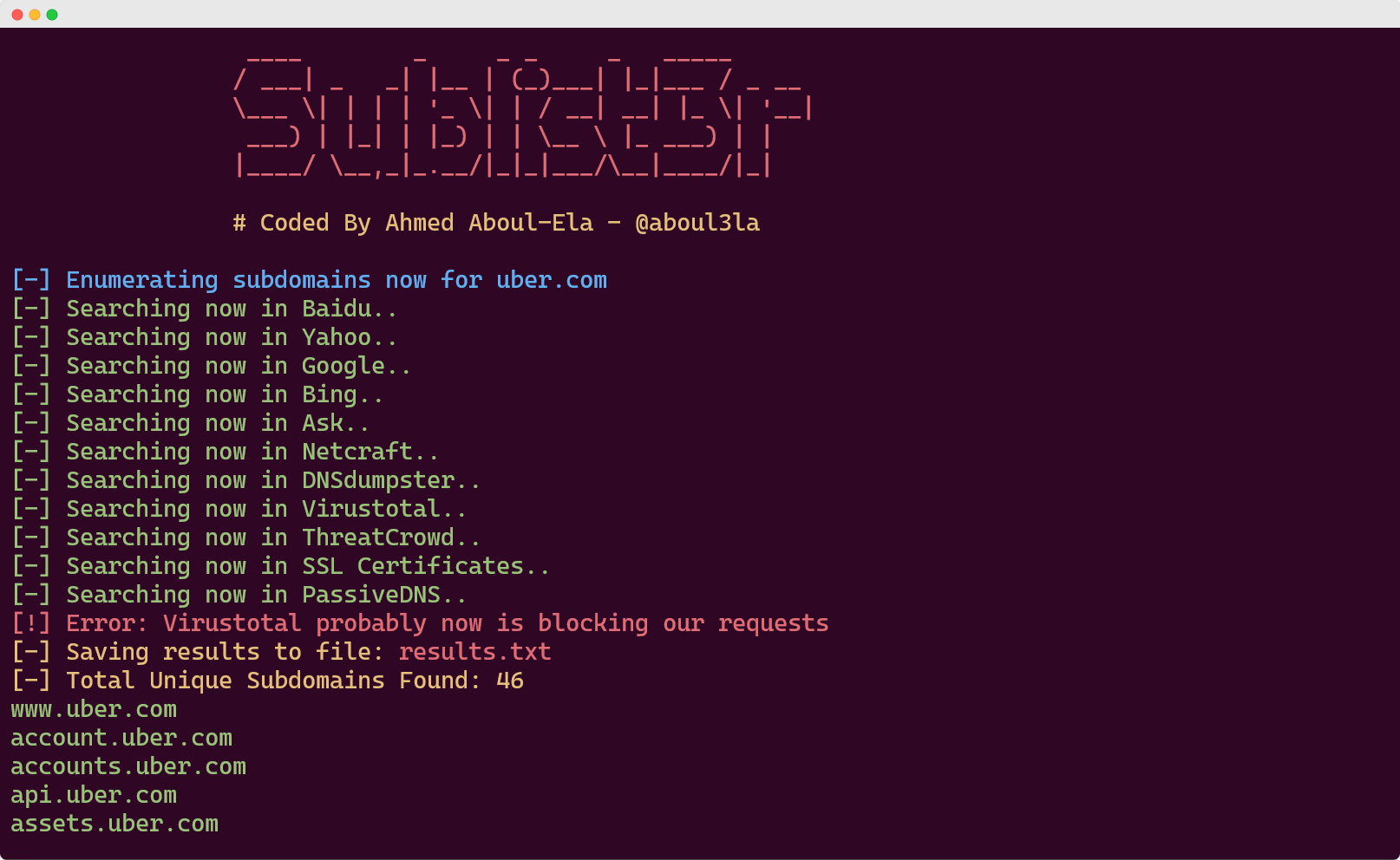
Sublist3r's strength lies in its search engine integration. While newer tools focus on API-based sources, Sublist3r excels at finding subdomains that appear in search results, forums, and public websites.
Tool #5: Chaos - ProjectDiscovery's Crowdsourced Database
Chaos isn't just a tool - it's a massive crowdsourced database of subdomain information. Think of it as the Wikipedia of subdomain discovery, built and maintained by the bug bounty community.
The database contains millions of subdomains collected from various sources and continuously updated by security researchers worldwide. What makes Chaos special is its focus on active subdomains - not just historical data.
Installation:
go install -v github.com/projectdiscovery/chaos-client/cmd/chaos@latest
Usage:
chaos -d target.com
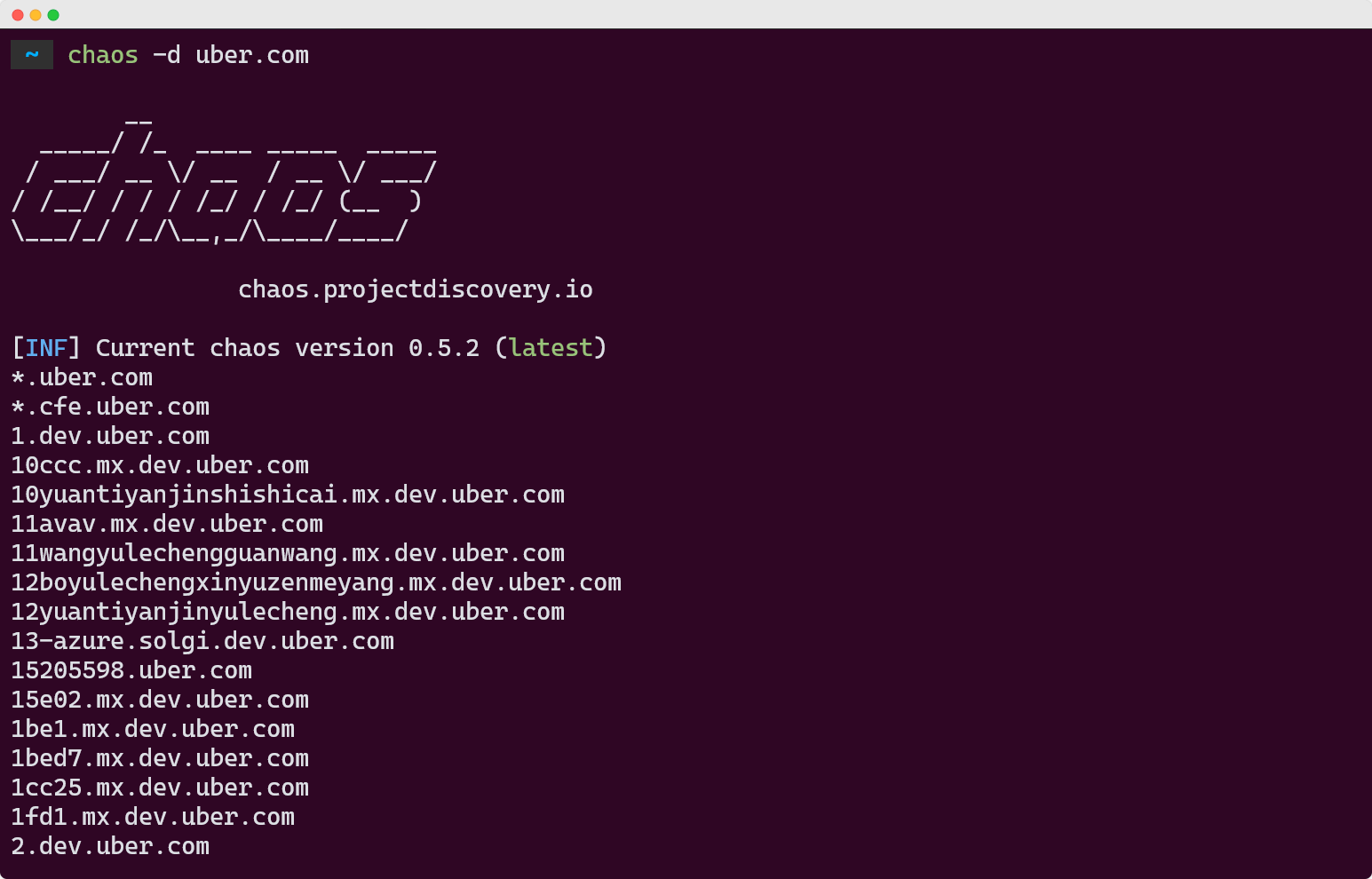
API Integration: You'll need an API key from chaos.projectdiscovery.io to access the full database.
Chaos excels at finding subdomains that other tools miss. Because it's crowdsourced, it often contains subdomain data from private bug bounty programs and internal reconnaissance efforts that aren't available through traditional sources.
Your Next Steps to Subdomain Mastery
Subdomain discovery is both an art and a science. These five tools give you the scientific foundation, but the artistry comes from understanding your targets and adapting your approach.
Start by installing all five tools and running them against a test target. Compare the results and notice how each tool finds different subdomains. This overlap and uniqueness is exactly why professional bug bounty hunters use multiple tools.
Create a simple bash script that runs your favorite combination of tools and deduplicates the results. Automation saves time and ensures you never miss a tool in your reconnaissance workflow.
Most importantly, remember that subdomain discovery is just the beginning. The real value comes from what you do with those subdomains once you find them. Each discovered subdomain is a potential gateway to vulnerabilities, sensitive data, or system access.
Happy hunting, and may your subdomain lists be long and your bug bounties be generous.